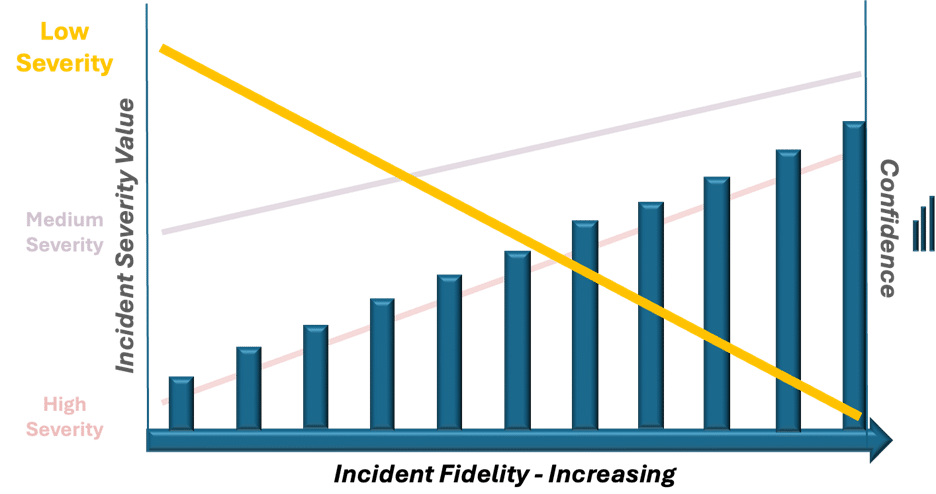
As incident fidelity increases, the value of low severity alerts decreases.
Full Stop –
Beginning in the 1970s, with protection of government and military mainframes that comprised the ARPANET, each decade has brought progress in protecting computing systems from those that would do them harm. By the 1980s, personal computers expanded the threat landscape, with detections and protections developed for among others, Viruses, Denial of Service, Man in the Middle, and SQL Injections, now considered commodity attacks. The 1990’s saw the rise of Black Hat Hacking, Hacktivism, the formation of Threat Groups and exposure of Nation State Actors. With this, cyber defense evolved in the form of User Entity Behavioral Analytics (UEBA), and correlated detections captured through Security Information Event Management (SIEM) platforms.
Let’s pause a moment —
Notice how incident identification (as in fidelity) matured through each decade. Exponential development occurred with the advent of personal computers, where this is captured in changing nomenclature from Malware Signatures to Malware Detections.
It’s a great example as this acknowledges how early 1980’s Malware was able to be uniquely recognized by a rapidly identifiable Signature (Low level), compared to 1990’s Malware of the polymorphic variety, requiring complex means of Detection (High level).
But here’s the challenge —
It’s 2025, and in this decade, we are introduced to Generative AI for malware creation, requiring further enhancement to methods of detection; enriched by threat intelligence, for identifying and defending against malicious software, along with its associated tactics, techniques and procedures for deploying and enabling.
Meanwhile —
A historical volume of mundane malware still exists in the wild. This is low-value, low-level, signature based malicious software that is quickly mitigated, but none the less escalated to clients by lethargic MDR providers. Yes, utilizing the same platform-based rules, since their days as MSSPs, you will find these conventional providers serving as a factory, sending the same formatted tickets for Low, Medium and High Severity security incidents. All but ignoring that while their clients expend time and energy handling these low-value security alerts, apathy sets in, and less time is available for attending to viable threats in the form of High Severity alerts.
CyberMaxx Challenges Convention
As a Modern MDR Provider, CyberMaxx knows that decades of evolution with incident fidelity brings a parallel increase in confidence for identifying viable threats to an organization. This is a continuum CyberMaxx maintains through Threat Research, Continuous Threat Exposure Management and Offense Fuels Defense, bringing learnings from the Threat Response Team and Offensive Security Group in creating a protective fabric for our clients.
CyberMaxx subscribes to the principles shared in this article, that the value gap between Low and High Severity detections has widened, and through this incorporates a Confidence Index, identifying the mundane, with enhanced operational standards and platform architecture for the purpose of handling Low Severity Incidents distinctly from those of High Severity. Here is what this looks like —
- Discernment in Detections for identifying PUA (Potentially Unwanted Application), PUP (Potentially Unwanted Program), and other commodity Malware, that present as Low Severity Alerts, with confidence.
- Capturing these isolated Low Severity Alerts in the form of a report, visible on the CyberSight Portal, where they can be viewed collectively for patterns and thresholds.
- Stop ticketing isolated Low Severity Alerts—use the CyberSight report as the Modern MDR review standard.
- Continue to use Low Severity Alerts where they are correlated with Medium and High Severity Investigations. It’s important to distinguish for Low Severity in the lead-up to a more serious attack. It’s the commodity Low Severity in isolation that we move to a report, and away from individual tickets.
- Change the mindset that a large volume of tickets of the Low Severity classification is synonymous with protection. This value-less approach is in the domain of MSSPs, who are alert forwarding and ticket factories. We respect our clients and are here 24x7x365 to take on the work of protecting their business, not making work for them.
CyberMaxx continues to evolve our MDR service, enhancing protection of our clients, through innovation and contemporary investigative methods that outpace our competition, who are limited by their legacy platforms. We are a tech-enabled services company, bringing a talented team of analysts and threat hunters who defend against, and pursue for, all those that might do our clients harm. Separating the signal from noise by uniquely managing low severity alerts to a report reduces apathy and keeps us collaboratively focused on credible threats. This is what it means to be a Modern MDR cybersecurity provider. This is what you receive as a CyberMaxx client.



