The Conti ransomware gang recently published an “EDR Tier List” from their page on Twitter (Now X), ranking popular Endpoint Detection and Response (EDR) solutions based on how effective they have been, and on the difficulty of bypassing during attacks.
Shared by @PsExec64, the list uses a tiered system from S Tier to LOL.
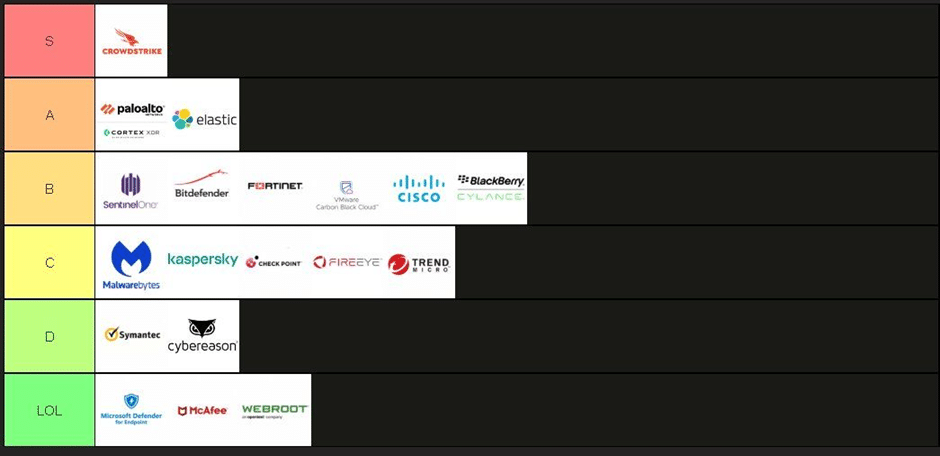
Tier breakdown below:
· S Tier: The toughest EDRs to bypass, representing some level of resistance.
· A Tier: Strong performers that require effort to defeat.
· B Tier: Middling, attackers take them seriously but workarounds exist.
· C Tier: Weak enough to be dismissed in most serious attacks.
· D Tier: Almost irrelevant, relatively trivial obstacles.
· LOL Tier: Reserved for tools considered laughably ineffective in real-world breaches.
One surprise was the placement of Microsoft Defender for Endpoint (MDE) in the LOL Tier, sparking discussion among security professionals. While MDE has solid detection capabilities when properly configured, it’s likely that Conti’s low rating reflects how frequently they encounter it in default or poorly secured deployments. Many organizations rely on MDE out of the box without enabling its advanced protections, making it far easier for threat actors to evade — and justifying the “LOL” label in Conti’s eyes.
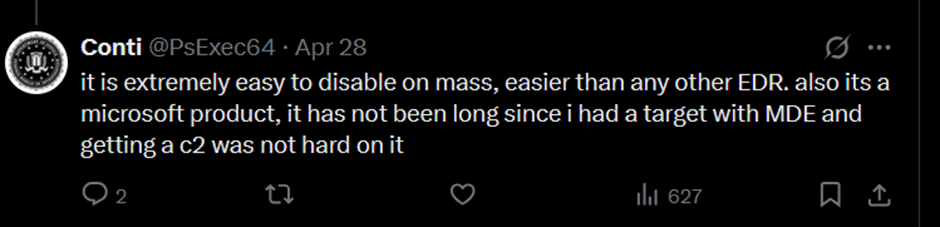
Later, the group mentioned that they can bypass all EDRs listed – mentioning that some require more work than others.
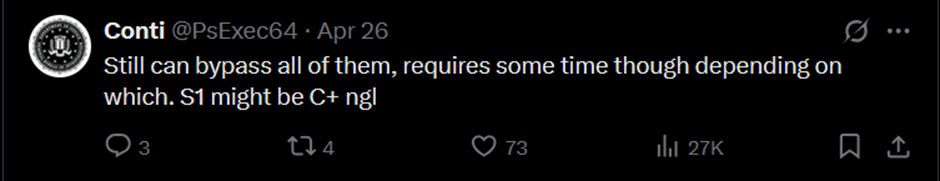
The post created a lot of discussion in the comments, with various users pointing out benefits and flaws in various platforms.
The key takeaway here is that configuration matters just as much as product choice. Strong tools can become weak if left in their default state and not used to their full potential.



