In digital forensics, analysts are immersed in investigations, meticulously examining the intricate virtual trails left behind by cunning cybercriminals. Amidst the complexity of these investigations, it is not uncommon for certain artifacts to evade detection, concealing invaluable clues that are deceptively apparent.
One such artifact, the .wget-hsts file, quietly resides in the depths of a user’s home directory, harboring valuable insights for those astute enough to recognize its importance.
The .wget-hsts file, born as a byproduct of the widely used wget utility, may appear inconspicuous at first glance. However, within its seemingly innocuous contents lies a tale of post-exploitation activities that unfolds in the realm of threat actors and their malevolent intentions. These actors frequently employ wget to download malware or further tooling onto compromised systems, enabling them to expand their foothold within an infiltrated network.
Acknowledged as a crucial forensic indicator, the significance of the .wget-hsts file cannot be overstated. Its presence has caught the attention of renowned cybersecurity organizations, including Mitre, whose ATT&CK Matrix categorizes adversary techniques and tactics. Specifically, the use of wget for downloading malicious payloads is meticulously tracked under T1105, aptly named “Ingress Tool Transfer.”
What is wget and how can it be used for forensics?
The wget utility is a command-line tool commonly used for retrieving files from the web. It supports various protocols, including HTTP, HTTPS, and FTP. When using wget, a file named .wget-hsts is created in the user’s home directory by default. This file stores the HTTP Strict Transport Security (HSTS) information.
HSTS is a security mechanism implemented by websites to enforce the use of secure HTTPS connections. It instructs web browsers to communicate with specific websites only through encrypted connections, thereby protecting against certain types of attacks, such as man-in-the-middle attacks. The .wget-hsts file records HSTS information for the websites visited by the user via wget.
In a forensic context, the .wget-hsts file can serve as a valuable indicator. Threat actors often engage in post-exploitation activities after compromising a system. One common activity is to download malware or additional tools onto the compromised system to facilitate their objectives, such as maintaining persistence, exfiltrating data, or launching further attacks.
By using wget to download malicious files, threat actors may leave traces in the .wget-hsts file. The file could contain entries indicating the URLs of the websites from which malicious content was retrieved. These URLs can provide insights into the attacker’s infrastructure, potential command and control servers, or sources of malware.
In the ATT&CK Matrix, the technique referenced as T1105 is “Ingress Tool Transfer” and specifically pertains to the use of legitimate tools like wget for downloading malicious files or tools onto a compromised system.
Unveiling the Secrets of the .wget-hsts File
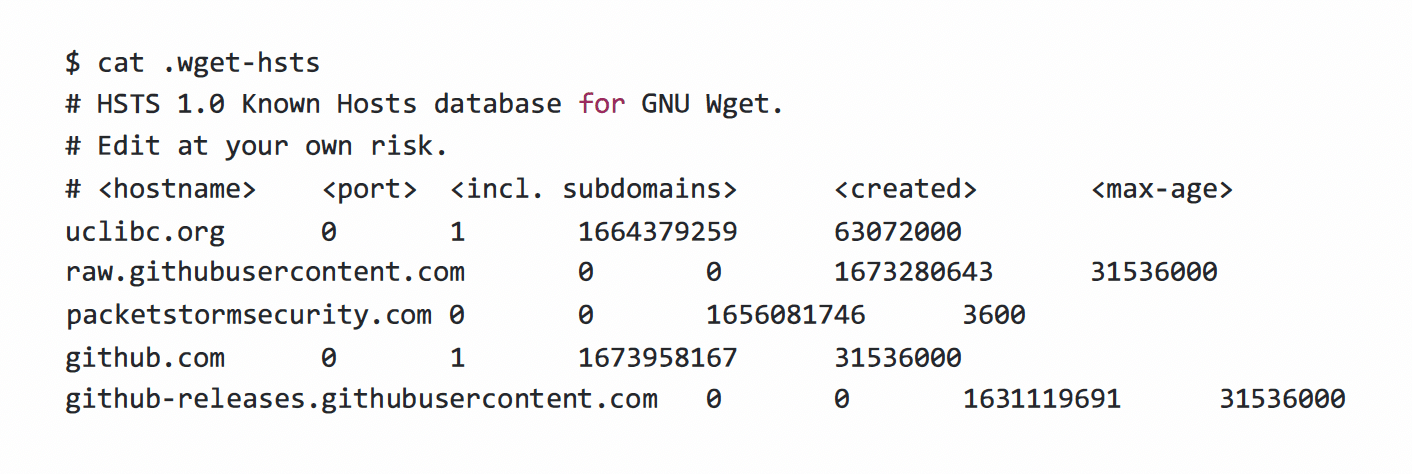
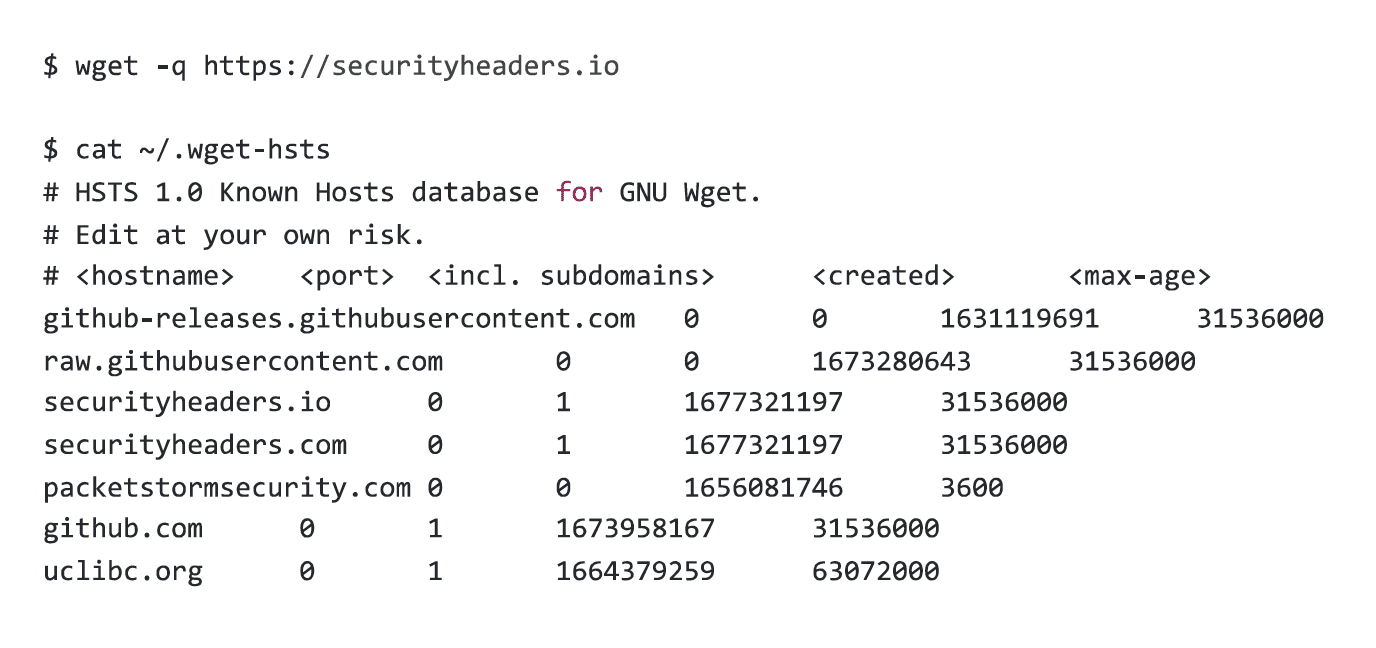
When wget is ran for the first time against a HTTPS webserver that sets a HTTP Strict Transport Security header, an entry is made into its HTTP Strict Transport Security database – logging the hostname, a field for “port”, if subdomains should be included (from the header value), the timestamp of when the request was made (in Unix time format), and the max-age value of the HTTP Strict Transport Security header sent by the server.
This database is usually stored in a file named .wget-hsts in the home directory of the user who invoked the wget utility. Below, we outline its fields.
The hostname field is self-explanatory – it is the hostname which was connected to.
The port value is often zero (0), which tells wget to use HTTPS for all webserver ports at that hostname in future.
The include subdomains field depends on what the server header sends. This tells wget if the HSTS rule should apply to subdomains or not – and is a 1 or O value.
The “created” field is a Unix timestamp of when the entry was created. This is of interest to us.
The max-age is set by the servers strict transport security header, and tells wget how long to apply the HSTS rule for.
Below is an example of the files contents.
What can we learn from this file?
This file tells us that wget was used on the host at specific times to connect to specific hostnames. This is incredibly useful for building a forensic timeline in some circumstances.
For example, if there was an entry like so:
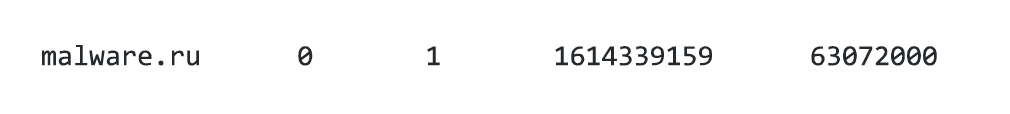
This would tell us that wget was used to download “something” from the host “malware.ru” at Fri Feb 26 2021 11:32:39 GMT +0000.
We then have a possible date to work with for further investigation – you can then consider running the find utility to locate files created, accessed, or modified during whatever time window after the .wget hsts entry was created. I usually go with an hour-long window to start.
Countermeasures
For an intruder, avoiding this logging is actually trivial. wget supports two arguments that will avoid creating this file. –no-hsts will tell wget to not bother with HSTS, and –hsts-file=/dev/null will tell wget to use the /dev/null device as its HSTS database.
Consider the differences in output of the three commands below. I used Scott Helme’s excellent Security Headers site as an example, because if anyone was going to have HSTS set up right, it was gonna be Scott.
You will also notice – if there is a 30x style of redirection (as is the case with securityheaders.io), the original hostname supplied, and the redirect target, will be logged.
Running with the –no-hsts argument, logging is avoided.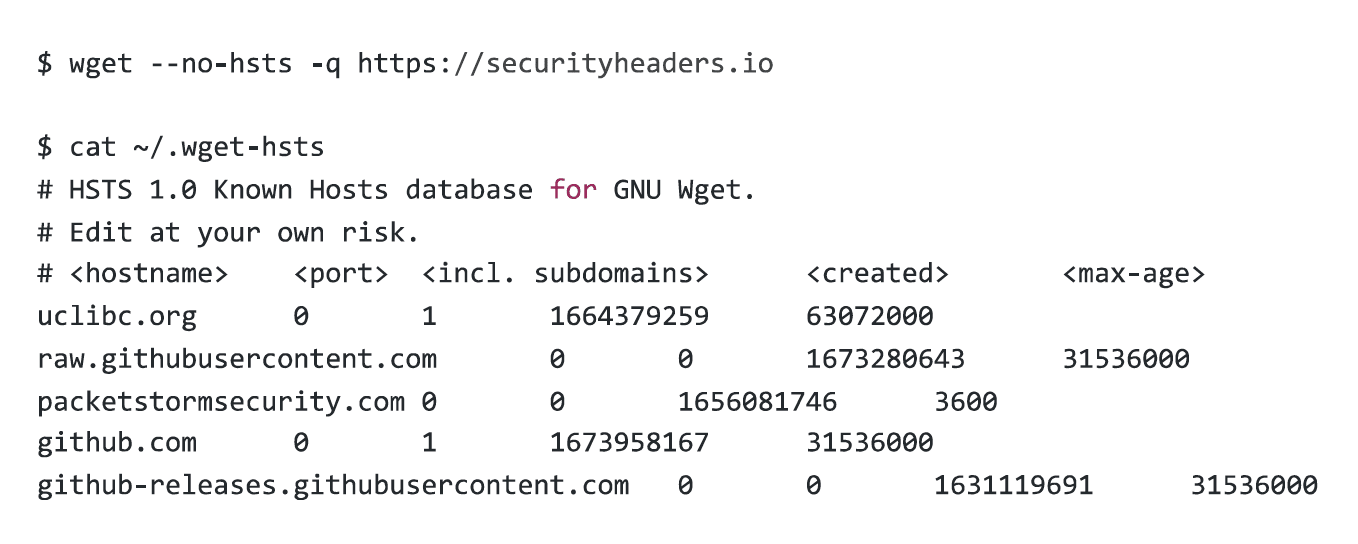
Setting the hsts file to /dev/null – logging is avoided.
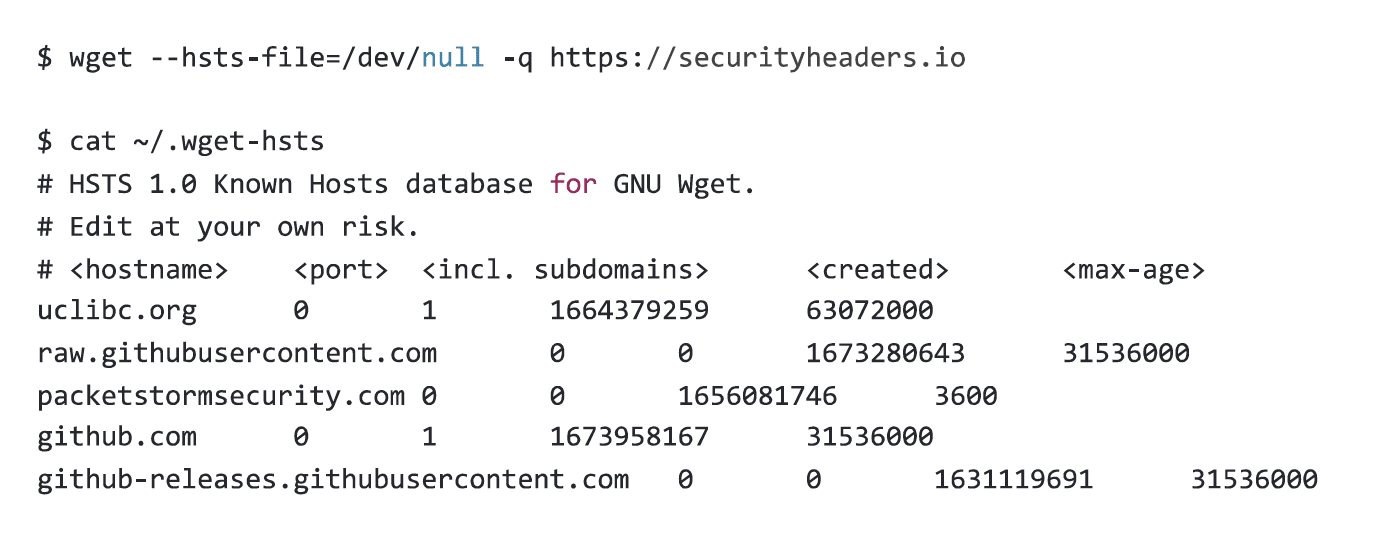
Finally, running it with the normal arguments – the hostname will be logged with the appropriate timestamp.
Counter-Countermeasures
If you have process/commandline monitoring (for example, via an endpoint detection and response solution), alerting on any invocations of wget that pass the –hsts-file or –no-hsts flags can surface attempts at avoiding logging. This is, however, a noisy indicator.
Conclusion
The .wget-hsts file, created by the wget utility, can be an important forensic indicator when investigating post-exploitation activities. It can potentially reveal the URLs of websites used by threat actors to download malware or other tools onto a compromised system. This file is acknowledged as a valuable artifact in the field of digital forensics and is recognized in the Mitre ATT&CK Matrix under T1105.
While on its own it doesn’t give you a full picture of anything, and attackers can avoid creating it by passing certain arguments to the tool, it can be powerful evidence when combined with other data.



