In a recent disclosure, a method to bypass SentinelOne’s anti-tamper protection by abusing its upgrade process through an .msi file has made the lives of infosec professionals quite interesting over the past few days. The technique documented allows a threat actor to disable protection on an endpoint, clearly a significant issue. While this is dangerous (and we’re not trying to downplay its significance – it can turn off the agent) it is not the most alarming thing happening in endpoint security right now.
Let’s unpack this—then put it in perspective.
The Good, The Bypass, and the Ugly – in Reverse
Stroz Friedberg (AON) identified a technique where the SentinelOne agent’s upgrade process could be hijacked. In our reproduction of the technique, execution in both hands-on keyboard and scripted fashions is achievable, and skill-wise barrier to entry is very low. When done properly, the MSIExec process will kill all former SentinelOne processes, and in the right moment, an attacker can simply kill the MSIExec process as well. This results in protections being completely disabled without triggering anti-tamper controls.
In response, SentinelOne issued mitigation guidance, which we tested. We are confident that enabling “Online Authorization” will remediate the issue. In conjunction with its simplicity, the bypass is concerning, but there are actually a few threads to unwind at this point.
Firstly, SentinelOne is doing everything they can to respond appropriately. We’re actively working with them to ensure detection for this activity is robust and can be identified before the agent is disabled. We say that because engaging the “Online Authorization” feature may not be possible for environments where SentinelOne is not the platform that controls upgrades. Enabling this feature when popular RMM tools or SCCM are used to that end means upgrading will fail. For clarity, this will not kill an agent, but it will not upgrade as intended. This creates a few more issues to unwind for upgrades and stragglers who weren’t online during an upgrade cycle.
Alternatively, we can deploy live updates to active agents. However, this creates a different risk where a live agent upgrade causes a host failure. Creating an impact event of its own. For this reason, CyberMaxx treats the endpoint policy on a case-by-case basis, and we work as closely as possible with our clients to make sure we’re doing what’s best to secure their environment, while enabling business continuity.
We should take this opportunity to have a breath and review what’s necessary to exploit this bypass. A threat actor must gain access to an endpoint through an attack; from there, the TA must escalate appropriate privileges to install software; and as of this moment, GUI access is required (at minimum, if a command interface is the attack method, threat actors may need to disable/bypass User Access Control (UAC) prompts to execute). In any event, there are a few opportunities to gather telemetry, which alert us to the threat actors’ presence and enable our SOC to remediate and eradicate the threat before it becomes an impact scenario. If the undisclosed AON client had CyberMaxx protection in place, it’s highly likely that the attack would have been remediated prior to becoming such an event.
This author believes the reason that babuk, the TA referenced by AON, resorts to this bypass methodology is in fact the protections SentinelOne had in place by default. It’s evident that they already ran into issues with SentinelOnes default password protection on the agent [see “unload” command in this AON article].
Let’s not miss the forest for the trees. While debate over EDR agent behaviors takes place, there are larger systemic exposures that are being actively exploited right now. The good news is, we’re catching them!
Search Engine Optimization Hijackers dropping malware that will quickly attempt to bypass endpoint security products to drop info/cred-stealers are all the rage in malware. Our SOC has observed popular pivots off these techniques, which are lightning fast and plentiful, but our Threat Response Team and Detection Engineers have already prepared for them.
Two examples we’ve observed recently are a multi-stage (9 stages) initial access payload to stop Windows “Anti-Malware Scan Interface” (AMSI-Bypass) and a similar (12 payload stubs) obfuscated command to stop the “Event Trace for Windows” (ETW). Both of which are critical processes for EDRs to do their job.
In this example, a user installed an illegitimate, but free PDF software to their host. Upon double-clicking for install, the application launched a hidden process. This web untangled itself into a multi-staged payload, which CyberMaxx was able to observe. Pictured below and 9th magical payload stub, a de-obfuscated AMSI-Bypass is observed coming to fruition in variable form:
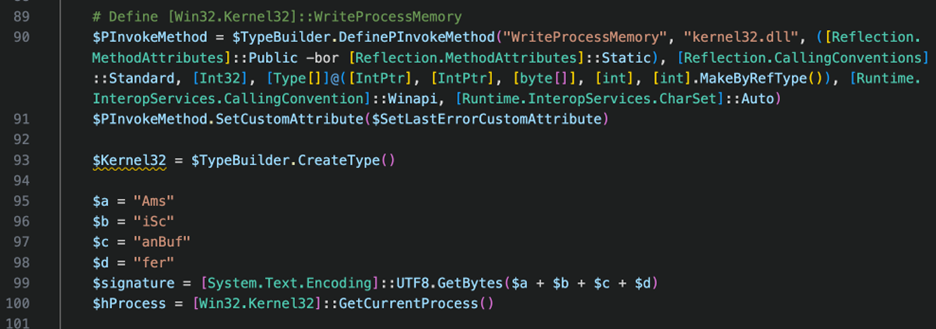
This bypass was attempted within seconds of initial access. Our SOC was able to react to this event, communicate the activity concisely based on several custom alerts it received. This painted a clear and full picture of what just happened, who it happened to, and what can be done to remediate the event. All of which were simultaneously communicated to the client, minimizing impact to a single user and preventing catastrophic damage from a threat actor proliferating in the environment.
The next example we have recently seen was observed during a “Click Fix” attack. Click Fix has been a valid technique for threat actors since the fall of 2023. This attack method has proliferated from phishing to Malvertising, Compromised Legitimate Websites, Social Media Sites, and the list goes on. Ultimately, malware embedded in a site asks a user to key in “Win + r” keys, bringing up the Windows run pane. The compromised page uses JavaScript to inject an early-stage malicious command into the user’s clipboard and asks them to paste it into the Windows run pane and hit “enter”. The user unknowingly triggers a cascade of obfuscated commands that, at breakneck pace, start staging malware on the victim’s machine. In this instance, we observed the following de-obfuscated PowerShell script snippet, which is meant to bypass ETW:
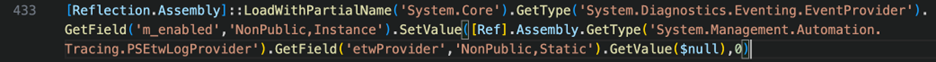
Our SOC was once again able to react to this event in a timely manner based on several alerts it received and prevent catastrophic damage from what would have surely resulted in an impact event to the environment.
Final Thought: What Matters
The SentinelOne bypass is an issue to be dealt with, but it’s only one late kill chain technique in threat actor playbooks. It’s not yet the first action, it’s not the quickest, and it’s not widely deployed. We need to remain focused on the reality of our industry: a layered solution allowing businesses to operate in an increasingly extremely hostile online world. Our clients should remain confident that CyberMaxx SOC, Threat Response, and Threat Research Teams are doing what’s necessary to prevent environments from becoming victims in that reality.



