Executive Summary
Have you ever wondered: What’s my Security Operations Center (SOC) or Managed Detection and Response (MDR) service actually doing? If so, it’s generally caused by sheer anxiety, or there’s a legitimate cause for questioning what your Security Operations Center is doing. I’m sorry for you in either event. But let’s take some time to rid you of those heart palpitations and questions. In this blog, we’re going to pull aside the curtain and show you what our Threat Research Team is doing to bolster the capability of our organization to react to events in your environment and make you more resilient to attack. We won’t just speculate about it – we’ll provide you with a real-world example from a very recent and relevant attack chain which would have resulted in an impact event had we not intervened.
“Those folks”
A SOC is a very complex part of an organization. There are SOC Analysts, Threat Hunters, Digital Forensics and Incident Response specialists, a Threat Response Team, Developers, Operations, and Code to keep it all running smoothly 24x7x365.
There are also groups of people you may know as “Threat Researchers”, “Detection Engineers”, or “Reverse Engineers”. I’m paraphrasing, but in his book Sandworm, Andy Greenberg describes members of this team as working in a “black room with no windows”. Sometimes members of these groups are combined into a “D.E.A.T.H. Squad”, which naturally stands for Detection Engineering and Threat Hunting Squad. What did you think we were talking about? When I first came into the information security community, I heard that “those folks run on caffeine and spite”, and I knew where I’d be drawn toward.
In all seriousness, this group performs critical tasks for any security organization. They focus on gathering data, digesting it, and providing “actionable intelligence” to key stakeholders in the organization. Along with bolstering the SOC, they’re responsible for part of the Sales & Marketing mission too (e.g., the very piece you’re reading).
A high-functioning team will take this intelligence and organize, categorize, and then codify it for use in the SOC. Detections are written based on activities observed as well as the team’s ability to surmise additional techniques to achieve the same result. So, it pays to have offensive and defensive minds working together here, because you’ll always have a better result when parties familiar with multiple methods to achieve a goal are in concert with people who know multiple ways to gather telemetry on said methods.
This is the case at CyberMaxx. Our Threat Research Team knows that relying solely on out-of-the-box technology like EDR or NIDS for detections is akin to playing chess with half the pieces missing – a grand master may survive against even a weaker opponent for a time, but not for long. The team is also responsible for understanding detection gaps like threat actors living off the land, abusing legitimate tools, bypassing or disabling tool sets, and for coming up with methods to cover the gaps! Let’s take a look at a concrete example to show you how this all goes down.
Real World Execution
In late 2023 and early 2024, our Threat Research Team became aware of a new attack that was being conducted against Microsoft Teams users. We documented a new social engineering attack being conducted by either sending targets an unsolicited Teams message or Email designed to entice the user into joining a quick Teams chat. Think “Hi, I’m from your IT provider BiiigTimeMSP, can you join this session quickly so we can get your system all updated? We’re behind, and your leadership wants this done ASAP!” Sadly, this proved tremendously effective at getting users to click links, which is the foot in the door that attacker is looking for. Once the session was established, it led to the installation of a persistence mechanism such as a legitimate Remote Management Tool like ScreenConnect or LogmeIn (again, living off the Land so as not to trigger AntiVirus or EDR Alarms). Worse, if the threat actor didn’t see an active EDR / Antivirus software, it led to dropping any malicious tool they want. In either event, it quickly leads to a potentially costly impact for the victim’s environment.
Here’s where those scurrilous rumors about caffeine and spite save the day. We do not like threat actors. So, when we write a detection for a Malicious Teams Session, we’re not just doing it for one or two that have occurred in the wild. Our team is constantly thinking of new ways to chain attack techniques together, along with the systems we have in place for telemetry collection. Along with that, we’re considering a range of other factors like relevance, the likelihood of that vector being deployed, etc. Ultimately, that leads to making a robust detection. In early to mid-2024, the Threat Research Team created a detection in response to analysis of the increasing threat to MS Teams as a risk surface. The team accounted for methods in the wild and the likelihood that tactics would continue to evolve. At that time, we were able to identify a unique commonality in a log parameter when threat actors executed this style of attack which had not been disclosed by other intelligence sources. In this case, the “Members” parameter in a specific event log always had strings of interest.
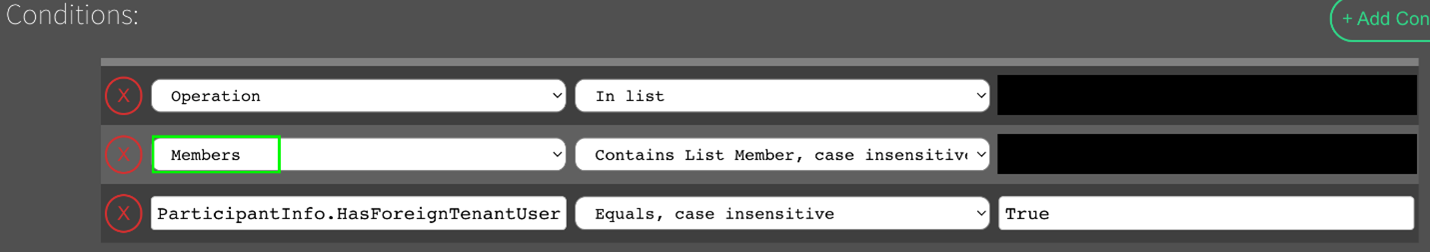
We simply added as many matches as we could, tested against them, and tuned the list to scale.
Early in May 2025, our SOC was alerted to this while no native Microsoft or EDR detections were raised. Pictured below is our SOAR detection for the MS Teams event.
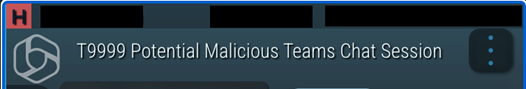
This is an alert that Microsoft clearly couldn’t deploy at scale. They likely know about it, but sadly have no viable method to tune their product at scale. On the other hand, CyberMaxx has developed and engineered for this scenario. Again, while we were never alerted to this activity from Microsoft natively, custom detections from our Threat Research Team alerted our SOC to malicious activity in a timely manner.
In accordance with our Detection Strategy and Threat Intelligence norms, all platforms we operate have a detection base made of custom queries meant to provide resiliency, depth, and indication of urgency for our SOC and Threat Response Team.
In the case at hand, four (4) supplemental custom detections worked in concert with the Teams Session watchlist, painting a clear picture of malicious intent to our SOC analysts. Pictured below are the additional alerts for enumeration, ingress, and persistence shortly after the Malicious Teams session.
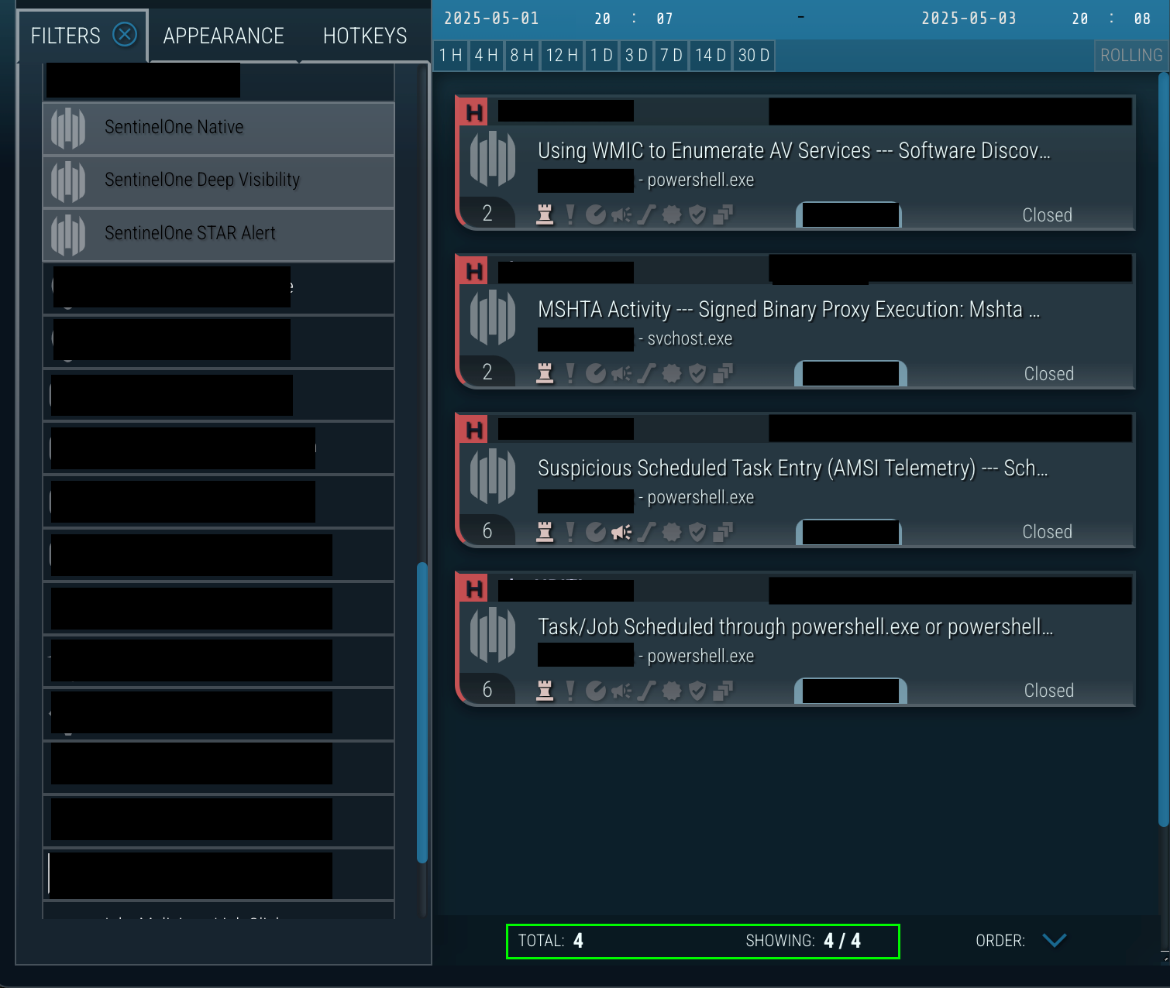
Once more, no native detections for the EDR platform were raised. It was not configured to alert because the threat actor was using approved tools for the environment and living off Microsoft binaries. This is the power of EDR, it provides rich telemetry that our experts can use to detect activity not natively alerted. EDR platforms would create alert fatigue if they alarmed on every living of the land tactic.
With everything observed in a short period of time, our Threat Response Team kicked off a remediation playbook, resulting in isolating the endpoint to quickly contain the threat, revoking the user’s M365 sessions, as well as resetting their credentials.
Final Analysis
The Threat Research Team at CyberMaxx takes the security and protection of any computer network extremely seriously. We don’t just drink the Kool-Aid of “think like an attacker”; we live it by studying them and emulating them with structured techniques. This is on full display in the case just described. It’s a necessity to have a team behind your SOC seeking to create Threat Intelligence and operationalize it in today’s world. The scale and scope of the largest product vendors will always have them leading the way to the best capabilities, but lagging when it comes to deployment at scale. When we can take their tools and customize them, we are able to fight that battle and win.



