Disclaimer: All links to dark web pages have been omitted as part of this report.
Sources: All screenshots have been taken by the Security Research team directly from LockBits Dark web pages.
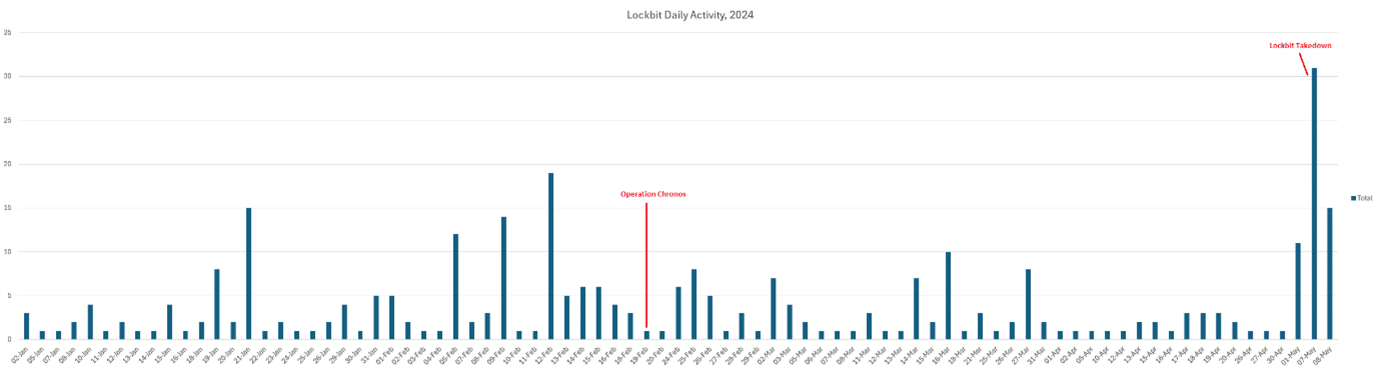
On May 7th, 2024, a joint task force by the US, UK, and Australia identified, sanctioned, and took down the person behind LockBits infrastructure, LockbitSupp. This has been tracked as Operation Chronos. The individual has been named as Dmitry Yuryevich Khoroshev.

The US has sanctioned the individual, details can be found in the US Dept. of the Treasury press release on the incident: United States Sanctions Senior Leader of the LockBit Ransomware Group | U.S. Department of the Treasury.
All property and interests that are in the United States or in possession or control of US Persons must be blocked and reported to OFAC. Multiple email addresses, cryptocurrency wallet addresses, and passport information have also been named as part of the indictment. The US Justice Department has currently filed 26 charges against the individual, among those including fraud and extortion charges.
However, some of the dark web sites are still currently active and show no signs of being under the control of Law Enforcement agencies. Sites under the control of law enforcement have changed the traditional loading screen of various cryptocurrencies into flags of the involved agencies. See evidence below:
Under control of Law Enforcement:
Under control of LockBit:

What this means is still unclear, this may be a case of not all sites having been updated to redirect to the law enforcement-controlled pages, however, new victims are appearing at the time of writing 09/05/2024 6:32 am EST / 11:32 UTC.
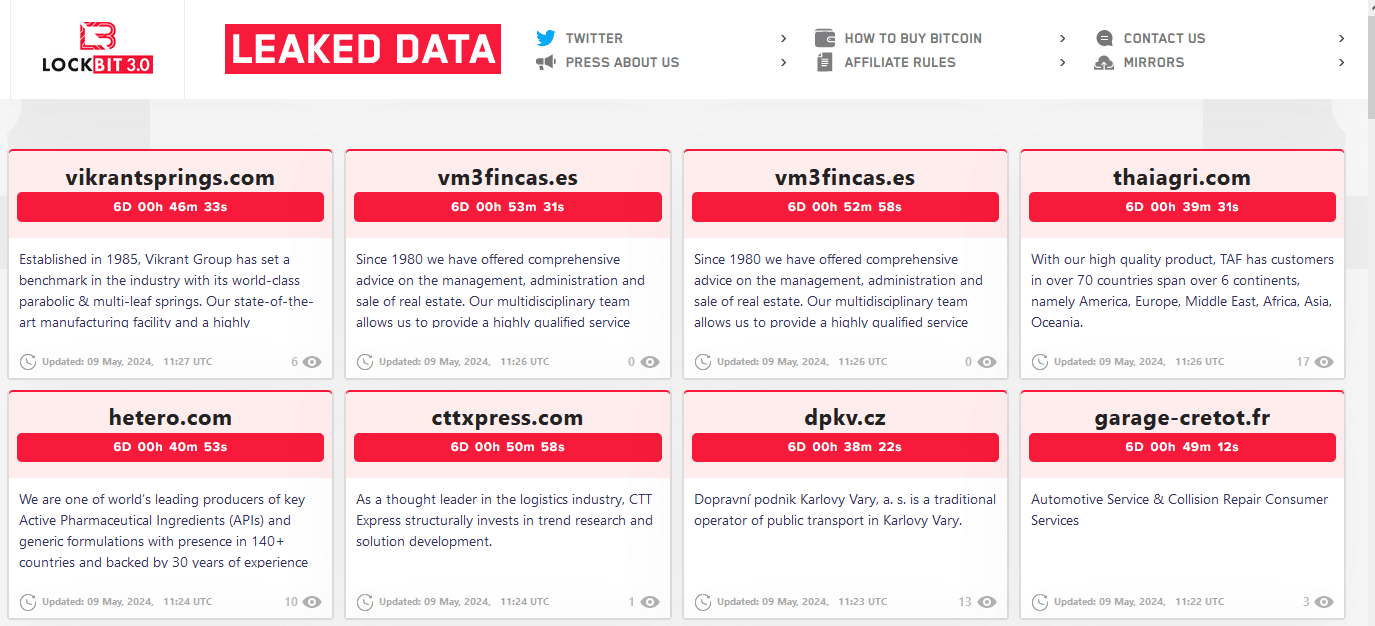
The pages that are under Law enforcement control no longer display victim information but rather display links and images related to the involved agency’s takedown and operations.
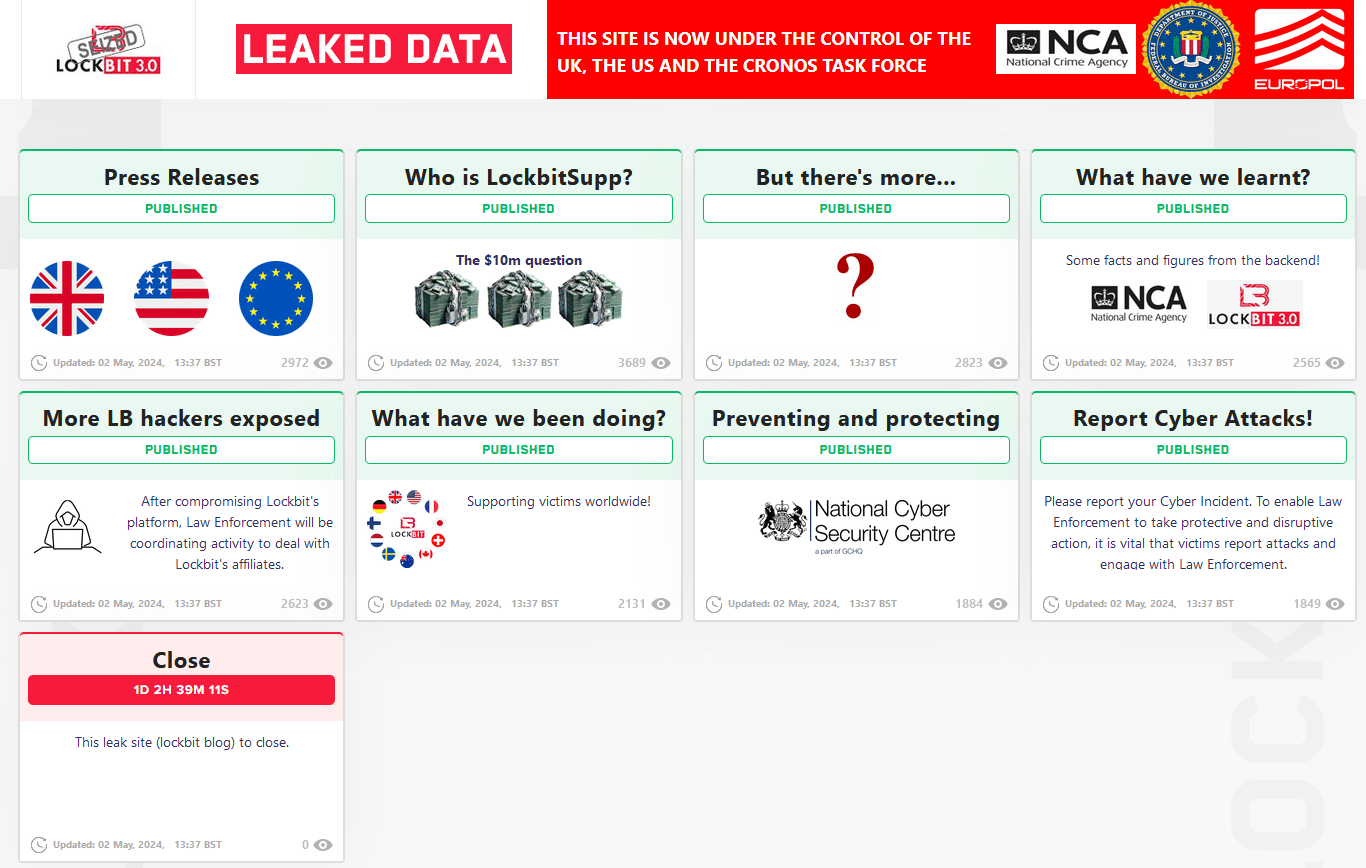
This section will be updated by the CyberMaxx team over the coming days by monitoring the sites that are still currently active for alleged continued activity as part of our ransomware tracking efforts.
LockBit Activity by month:
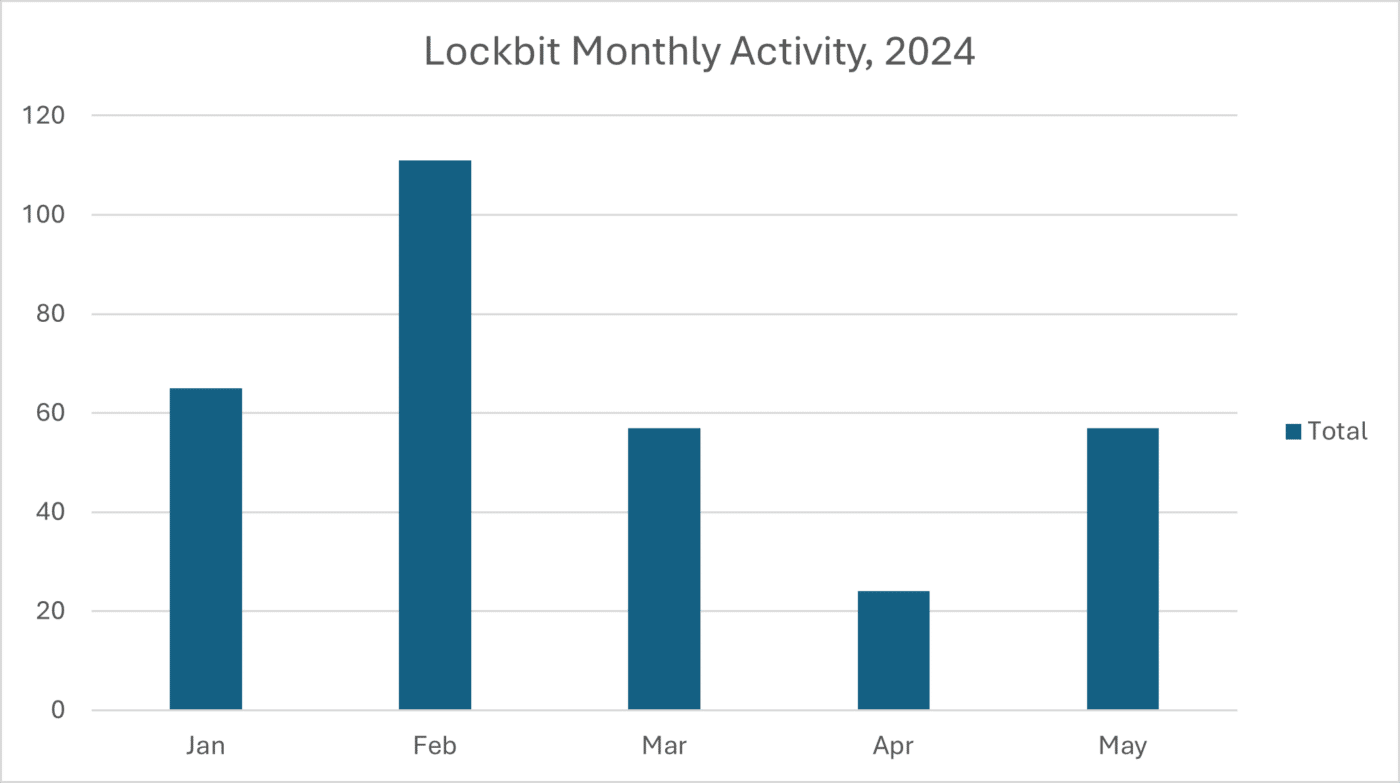
LockBit Activity and Notable Law Enforcement Takedown Attempts:
What was learned from the takedown?
As part of the operation, multiple user logins were identified on LockBit infrastructure, which is now being investigated as part of the next stage of the operation. These individuals have been presented below:
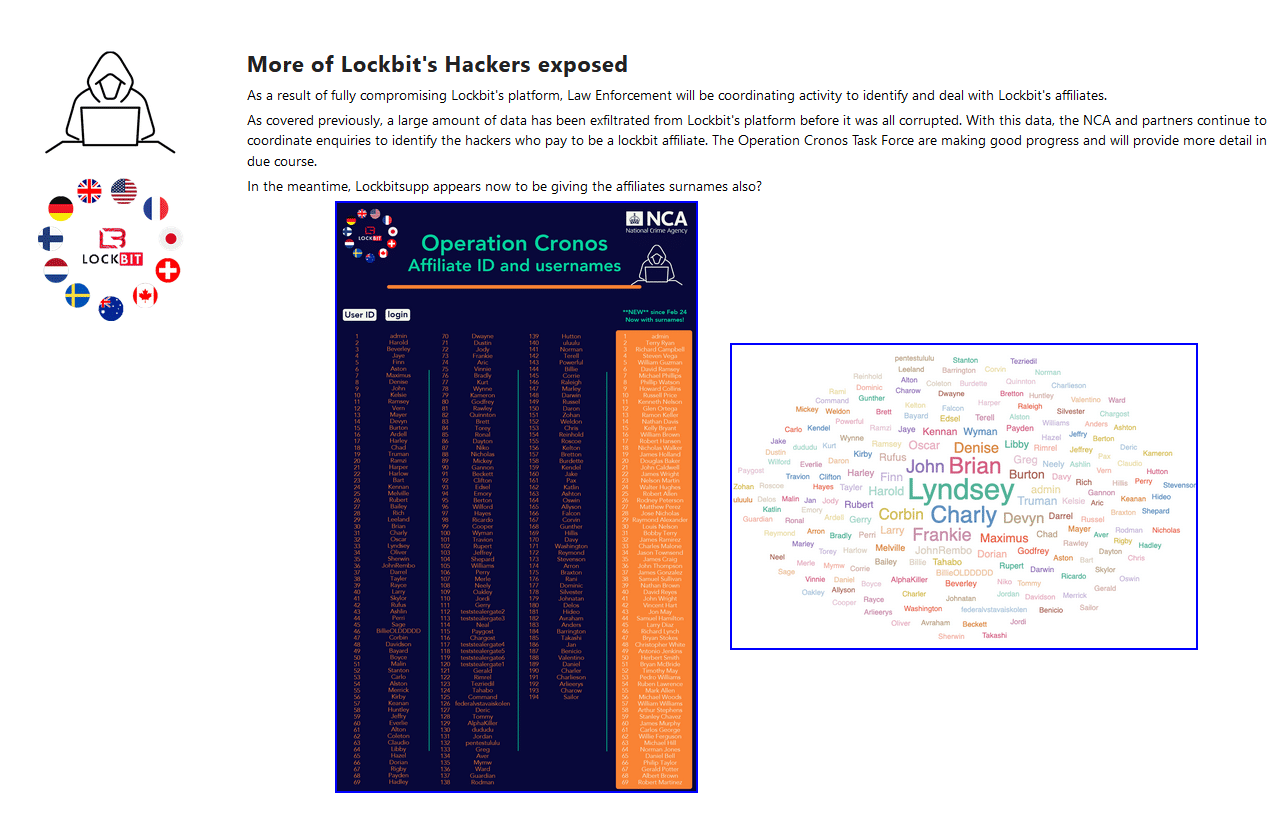
Closeup of the usernames used by Affiliates:
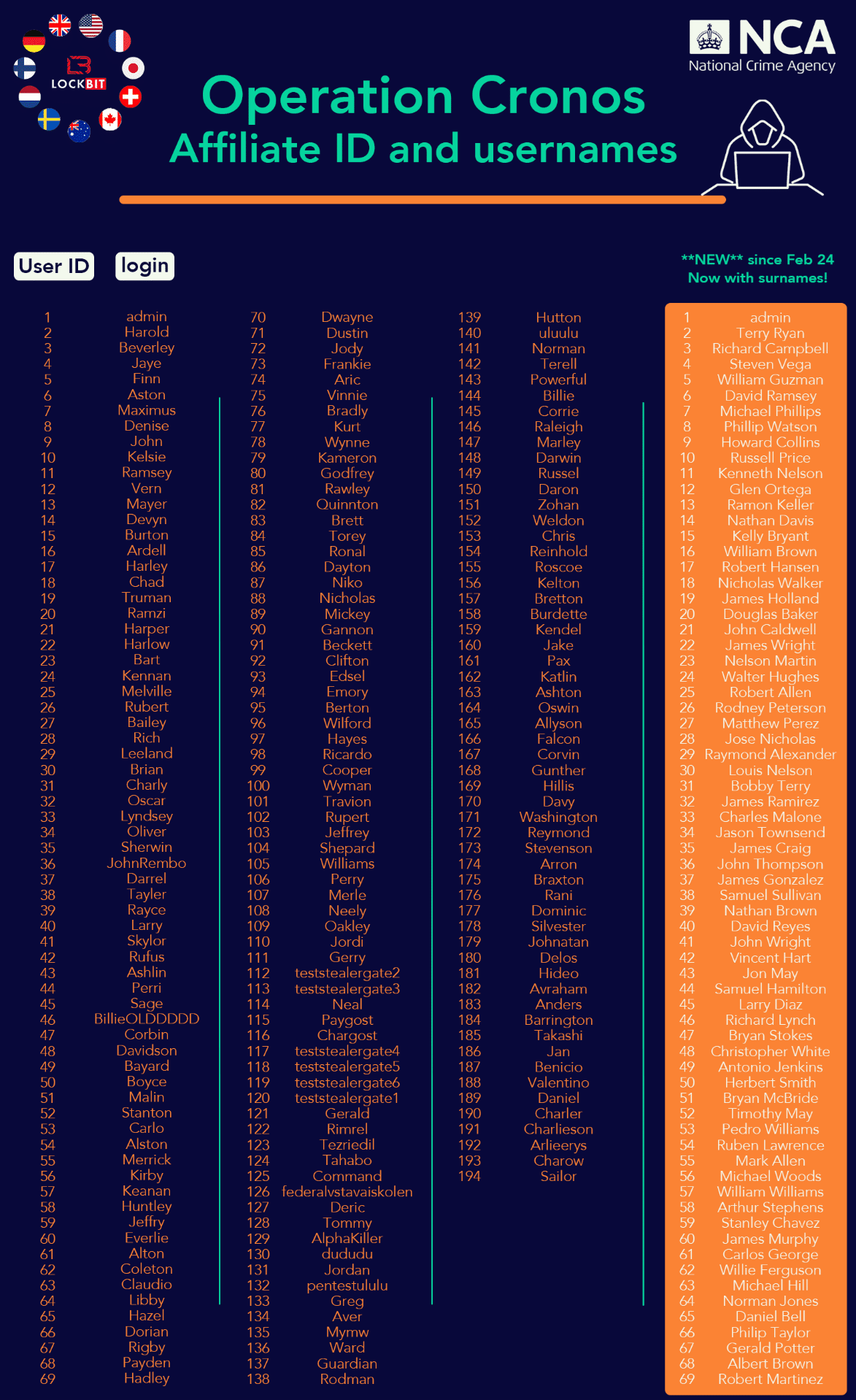
These names are not the real names of LockBit Operators, but rather the usernames of their third-party affiliates who worked with the group. The individual operational security of each user will not be put to the test with LE investigating who has been involved.
In a nod to ensure the information is factually correct, LE has asked LockBitSupp to get in contact if any information is not correct.

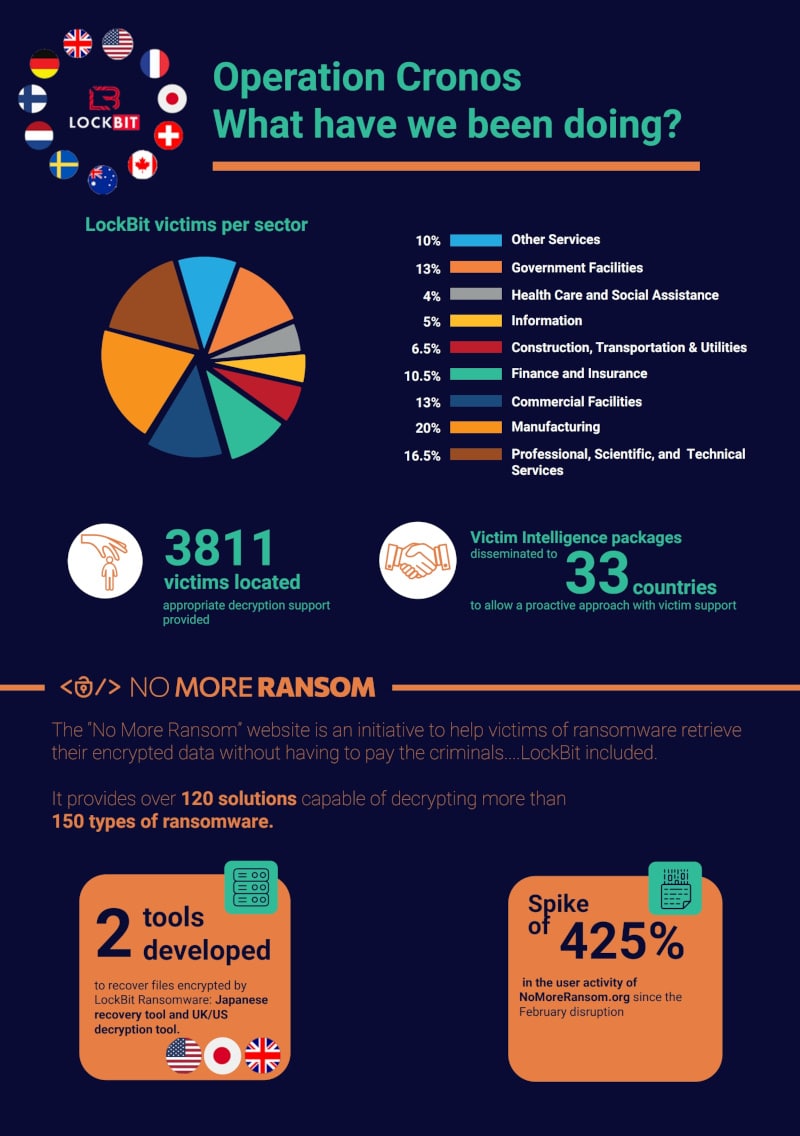
A breakdown has also been published describing the various industry verticals that LockBit victims reside in. A LockBit recovery tool has also been developed to help organizations recover from any negative impact caused by the ransomware group.
Reminder: The Japanese / Europol LockBit recovery tool is still available at https://nomoreransom.org