You hear about it constantly, and as a SOC leader, I see it firsthand: the evolving threat landscape and cyberattacks growing more sophisticated by the day. While maintaining a reliable IT infrastructure is crucial, security must be the top priority. That’s where the distinction between a Network Operations Center (NOC) and a Security Operations Center (SOC) becomes essential.
Though both play vital roles in IT management, the SOC offers deeper expertise, a stronger security-first mindset, and a proactive approach to cyber threats. Understanding these differences is key to making informed decisions about protecting an organization’s digital assets. Here’s a breakdown:
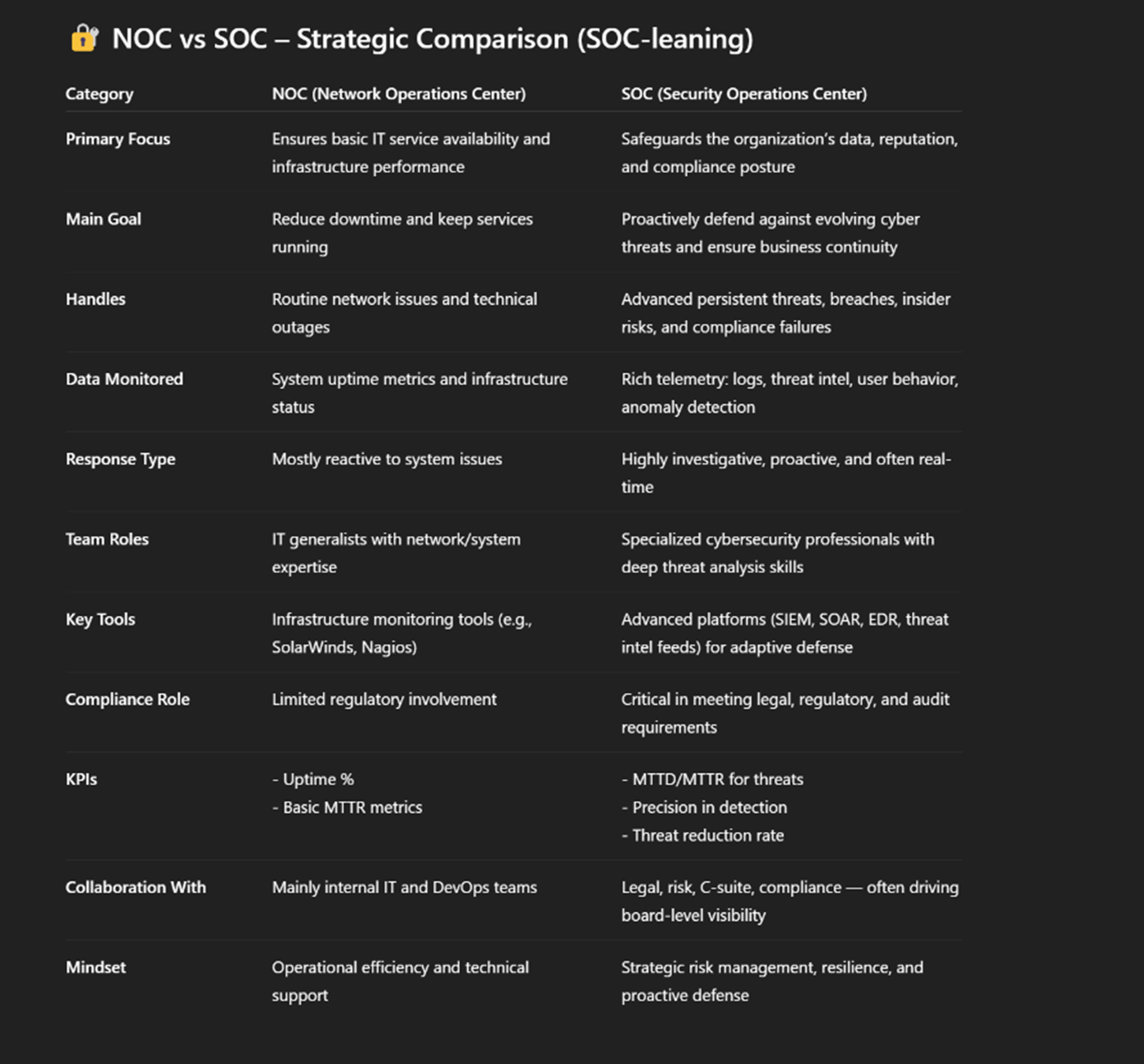
1. Primary Objectives: Availability vs. Security
The fundamental difference between a NOC and a SOC lies in their core mission.
- NOC: Primarily responsible for ensuring uptime, service reliability, and the overall health of the IT infrastructure. It focuses on resolving network issues, optimizing performance, and keeping business operations running smoothly.
- SOC: Dedicated to security monitoring, threat detection, and reducing the organization’s attack surface. Instead of simply maintaining systems, a SOC actively safeguards them from cyber threats through advanced threat intelligence and response strategies.
While a NOC ensures operational stability, it does not specialize in cybersecurity. A SOC, on the other hand, is built to detect and mitigate security risks, preventing costly breaches before they occur.
2. Data Being Monitored: Performance vs. Security Insights
The data each center monitors further demonstrates their distinct roles.
- NOC: Analyzes network traffic, device health, and system performance to identify inefficiencies and potential downtime risks. The goal is to maintain business continuity and optimize resources.
- SOC: Monitors security logs, user activity, and anomalous behavior that could indicate a cyberattack. SOC teams scrutinize patterns to detect signs of compromise and prevent malicious actors from gaining access to sensitive systems.
A SOC’s ability to analyze deep security insights ensures organizations are protected against modern threats, something NOC is not designed to handle.
3. Skill Set: IT Experts vs. Cybersecurity Specialists
While NOC and SOC teams share some technical knowledge, their skill sets are vastly different.
- NOC Professionals: Typically hold vendor certifications (such as Cisco and Palo Alto) and specialize in service continuity, networking, and general IT troubleshooting. Their focus is on infrastructure performance rather than security.
- SOC Analysts: Have security-specific certifications (such as Security+ and SANS) and operate with a security-first mindset. They are continuously updating their knowledge of emerging threats, leveraging Endpoint Detection and Response (EDR) tooling, conducting threat hunting, incident response, and analyzing security logs.
Cyberattacks require expertise beyond IT fundamentals— SOC professionals specialize in more nuanced areas than your typical NOC. They need to understand networking, endpoint, incident response, and preventive security measures. In addition to prevention, a SOC’s response model ensures that critical issues never sit in a queue waiting for attention. Because it is performed by experts in the SOC, response is immediate and focused on both understanding the full scope of the compromise quickly and taking swift action to contain and mitigate the issue.
The SOC Advantage: Security Beyond Just Operations
While a NOC is critical to keeping systems operational, it lacks the security expertise needed to defend against sophisticated cyber threats. A SOC provides continuous threat monitoring, advanced incident response, and proactive defense strategies, making it an indispensable asset for organizations serious about cybersecurity.
Modern security offerings provide advanced protection by providing a full scope of compromise evaluation and response capabilities within their SOC environment. Expedited response capabilities minimize the dwell time a threat actor has access to the environment, thereby limiting the damage that can be done.
Choosing SOC support means prioritizing protection, reducing cyber risk, and reinforcing an organization’s defenses. In today’s digital landscape, security is not optional, it’s a necessity.