Wait…CyberMaxx, don’t you offer network monitoring?
Wait, did we say that out loud?
There have been rumblings in the industry that intrusion detection systems (IDS) and intrusion protection systems (IPS) are on their way out as useful tools to protect organizational networks and devices.
“It’s obsolete!”
“Everything’s encrypted now!”
CyberMaxx feels that IDS and IPS are alive and well, especially when matched with a managed security operations center (SOC) (Ultimately that makes it more Network Detection and Response rather than just regular old network security) watching the traffic to make sure nothing slips in between the crack.
Although IDS and IPS solutions are designed to protect against potential threats, they can only be effective when properly deployed and configured – i.e. tuned to the specifications needed by the organization to weed out all the noise that could be hiding a bad actor’s ill-intended piece of malware. Traditional firewall-based security solutions are often not enough in today’s cloud computing and dispersed workforces.
IDS/IPS CliffsNotes: What Are They
Intrusion Detection System (IDS): Suspicious activity can be detected by analyzing data packets as they travel across a network. IDS is a tool that does this by identifying these suspicious packets and generating an alert. This system is passive, meaning it only detects and alerts, without taking any other action (Hint: this is where a mature SOC can help add years of experience to increase any organization’s security posture).
Intrusion Prevention System (IPS): IPS goes a step further by adding an active protection method of adapting to the threat and blocking the traffic from reaching the intended victim host.
There is no clear winner in the debate between IDS and IPS. Each has its own advantages and disadvantages, and the best option for a given organization depends on the specific deployment scenario.
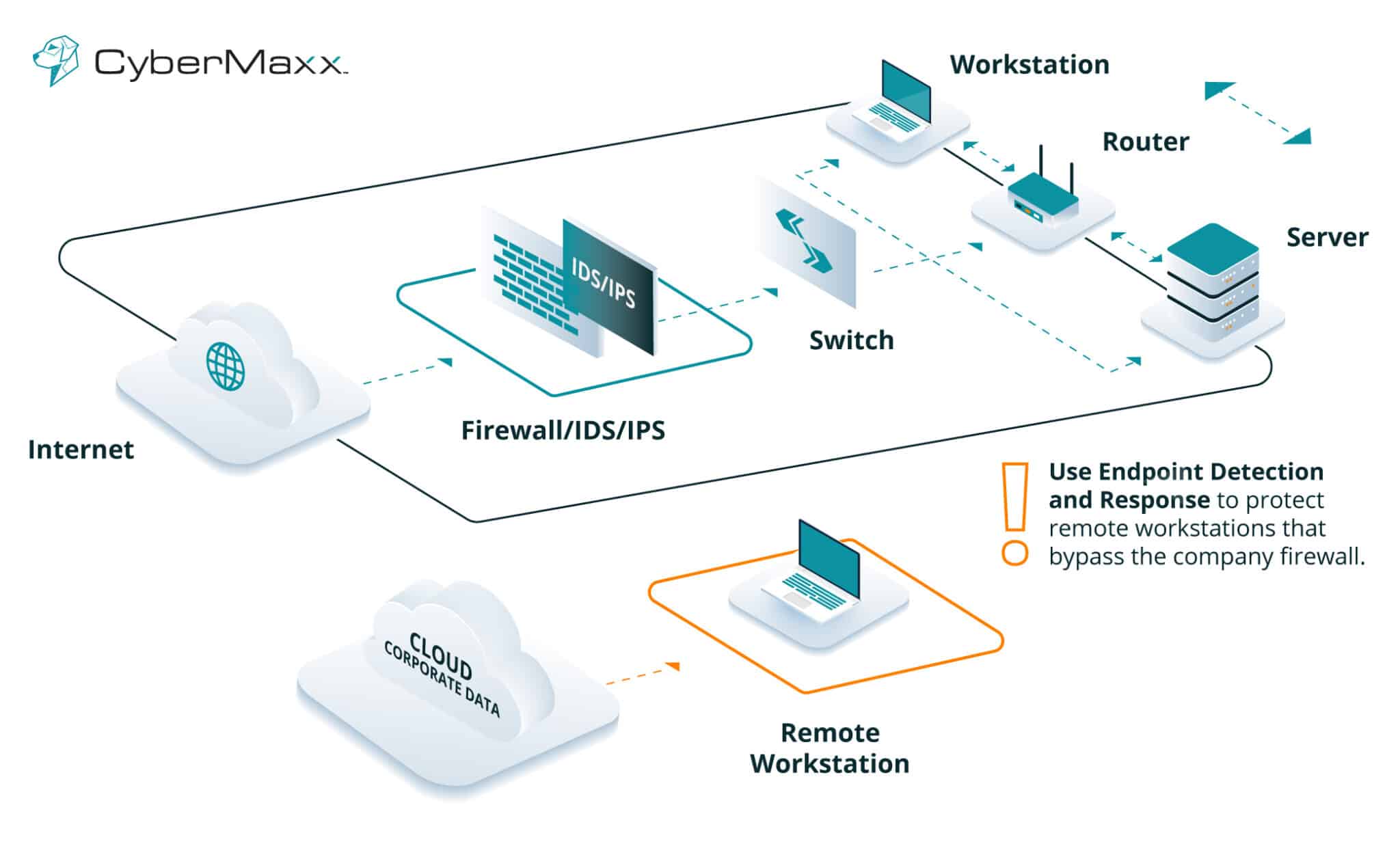
When IDS/IPS Isn’t Used Effectively
In order for IDS/IPS systems to be effective, it is important to understand a few of their inherent limitations.
IDS/IDS Rely on Signatures
This means that only known attacks are being watched for. Cybercriminals are constantly changing their methods, which makes it difficult for traditional security systems to keep up, and since these systems rely on signatures, which means that only known attacks are being watched for.
False positives and alert fatigue are big problems in the world of security. To combat these issues, many companies have sprung up that provide updated signatures and tune them to specific environments. However, even with these services, it’s still a lot of work to make sure everything is running smoothly.
An IDS will cause less disruption until properly tuned over an IPS – CyberMaxx typically recommends deploying in Detect only mode, tuning, and then when stakeholders approve, flipping it to block/prevent. It is always better to block an attack + alert on it than to simply alert and allow it to continue and business interruptions will be minimal when tuned properly.
Only the traffic that passes can be seen
We often see IDS/IPS implementations that provide a false sense of security to organizations because of poor network design. This is a serious problem that can lead to serious consequences.
Organizations frequently rely on unified threat management (UTM) systems, which work by routing all traffic through a central firewall. This allows the UTM system to monitor and scan all incoming and outgoing traffic for signs of malicious activity. By doing so, UTM systems can provide a high level of protection against a wide range of threats.
UTM Systems
A UTM setup is a great starting point for your security needs, but it leaves some major gaps in coverage.
A typical security setup does not include monitoring within security zones or between local workstations, servers, and remote workforces. This lack of monitoring can leave gaps in security that can be exploited by malicious actors.
Internal systems may have been breached by attackers who have compromised other systems, but unless the traffic from those systems passes through the IDS/IPS, it will not be detected.
IDS/IPS Used Effectively
There are weaknesses in any solution, but when the correct setups and configurations have been done properly, IDS/IPS are extremely effective.
To ensure that you’re getting the protection you need from these tools, take the following steps:
Get a Risk Assessment
Many organizations implement IDS/IPS simply to fulfill a compliance checkbox. But only having IDS/IPS in place may not be enough because most compliance requirements such as HIPAA, PCI, FISMA, etc. – require a risk assessment.
Vulnerability risk management is invaluable to quickly identify vulnerabilities and other risks organizational systems may be experiencing.
Bring IDS/IPS data into your SIEM for analysis
Security information and event management (SIEM) providers give you a way to monitor all activity in your environment and be alerted of any potential issues.
IDS systems generate logs, but do security teams often take the time to review them? By integrating IDS/IPS data into a SIEM solution, a better picture of what’s going on can be formed.
Most intrusion detection/prevention systems (IDS/IPS) generate a lot of false positives, which can be frustrating and overwhelming – this can lead to teams tuning out the noise.
Sprinkle in a little EDR
In today’s world, employees are often spread out across different locations. This can make it difficult to protect your company’s data since it is not always possible to rely on a corporate firewall.
Endpoint detection and response (EDR) is a security measure that bundles active detection and response into each workstation. This allows for quick and effective responses to any potential threats, as well as provides protection against workstation issues, IoT devices, BYOD problems, and more. Managed Detection and Response (MDR) or Managed Extended Detection and Response (XDR) systems provide an extra level of protection, making sure that all potential threats are caught and dealt with swiftly.
IDS/IPS + MDR/XDR = More Effective Security Coverage
Differentiating between well-tuned and poorly-tuned security tools can be difficult, but MDR/XDR provides the detailed information and correlations you need to make informed decisions.
In conclusion…
In the end…CyberMaxx thinks that IDS/IPS is still alive and well, even though the technology is now falling under Network Detection and Response (NDR). In fact, it’s a crucial component of our MAXX Network services we use to protect thousands of locations across the world for organizations needing our help.
There is a matter of making sure that everything is tuned well and that the technology is more effective when combined with EDR and SIEM technologies…not to mention matching it with a 24/7/365 SOC.
Have we convinced you that network monitoring is still a thing? Learn more about our services, specifically MAXX Network.



