I’m sure all of us (the ‘good guys’, anyway) are working hard to reduce the probability and the cost of cybersecurity breaches.
What professionals in the data security industry do is hard, and the ‘bad guys’ seem to be increasingly creative in devising ways to exploit vulnerabilities.
It’s what we at CyberMaxx like to call the digital arms race – bad actors are always trying to find new ways to infiltrate networks and devices with the latest technology and the ‘good guys’ are meeting the challenge to protect organizational assets.
The thing is, we know a lot about how to reduce the cost and the likelihood of a breach, thanks to reports like the IBM Security/Ponemon Institute annual Cost of a Data Breach Report, which has been produced each of the last 17 years.
If you’re out there fighting the good fight every day, there’s a lot of great information contained in these reports. Information that can help make the business case to secure funding and resources to save your organization time, money, and reputation.
This series is intended to highlight several key points and provide real solutions for this very real problem – It is not intended to be a full de-brief of the report, which we encourage you to read in its entirety.
Time
It turns out that the time it takes to detect, and then contain a breach has a big impact on the overall cost of a breach.
The time to identify a breach is the time it takes to detect that an incident has occurred. The time to contain a breach refers to the time it takes to resolve an incident after it’s been detected and to restore service.
To show where improvements can be made, let’s take a look at data showing the time to detect and contain over the past few years. In the chart below (Figure 8 from the report), we see that over the past seven years not much has changed significantly. The shocking number that pops out is that in 2022 it still took over 200 days on average* to identify that a breach occurred.
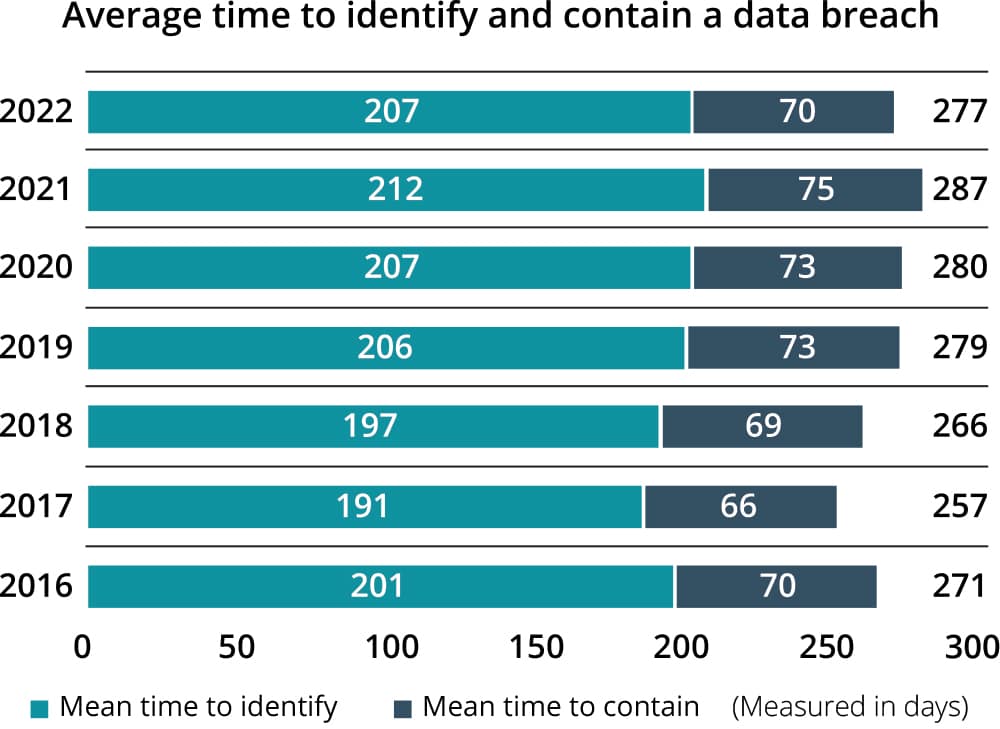
That’s more than six months just to detect the breach.
And another two months after detection to contain the incident.
Just imagine if better safeguards were in place in order to cut down on the amount of time a breach incident was active, or even better yet, prevent the breach from happening in the first place.
The Impact of Time on the Cost of a Breach
According to the report, a data breach lifecycle (total time between the breach, detection, and containment) of less than 200 days was associated with an average cost of $3.74 million in 2022, which is $1.12 million less than a lifecycle of more than 200 days ($4.86 million). So shortening the time to less than 200 days is fairly significant, a 26.5% reduction in the cost of a breach.
Apparently, Time is Money
At CyberMaxx, we believe that a data breach lifecycle of 200 days, while less expensive than a data breach lifecycle of more than 200 days, is still much too long (Remember, we’re still talking about half of a year just to detect).
While the referenced report does not calculate the savings of reducing the lifecycle by another 25, 50, 75, or even 90%, we believe early detection and response is one of the keys to a successful cybersecurity program.
CyberMaxx has extremely aggressive goals for detection and response, which we consistently exceed.
How? With a proven combination of people, process, and technology.
We’ll take a closer look at some of the key factors related to reducing the time to detect and respond, and therefore the cost mitigation of a breach, in Part 2.
* The IBM Security Cost of a Data Breach Report 2022 studied 550 organizations of various sizes impacted by data breaches between March 2021 and March 2022 across 17 countries and in 17 different industries




